Webinar
Don’t Panic! It’s Just a Cyber Incident
What's it like, in the hours immediately following a suspected cyber incident? In this recording, we ditch jargon, and dive into the messy, chaotic reality of incident response. Our 1:1 conversation includes war stories, lessons learned, and the hard-won wisdom gained from leading organizations through the fire. We pull back…
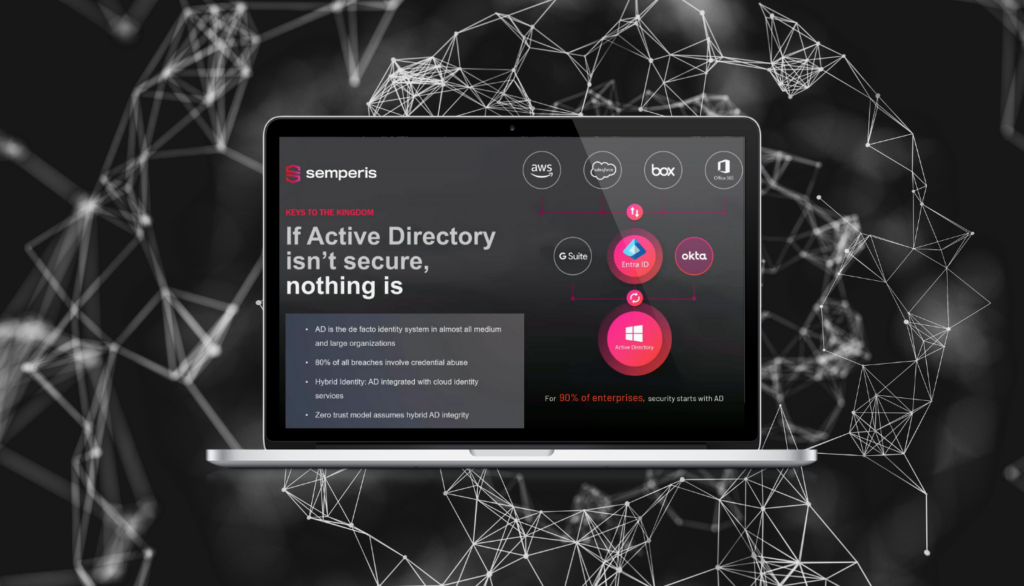
Securing and Recovering Active Directory from a Cyberattack
- Semperis
Cyberattacks against state and local government agencies, as well as critical public infrastructure, have soared over the past few years. Is your cybersecurity strategy ready for today’s attackers? From finding ways past MFA to hiding from SIEM solutions and security logs, threat actors have become adept at bypassing endpoint and…

Cyber Resilience 101: Top Tips for Active Directory Defense
- Semperis
A secure identity system is the foundation of your Zero Trust architecture. That’s why attackers regularly target Microsoft Active Directory (AD) and Entra ID. Gaining control of these identity systems can give threat actors near-total control of all your systems, access to sensitive data, and the means to devastate your…

Protecting AD: The Foundation of Your Zero Trust Identity Strategy
Cyberattacks are the most critical threat facing modern information technology. Most attacks start with identity compromise. For the past quarter century, identity in the enterprise has been synonymous with Microsoft Active Directory (AD). Therefore, AD is almost always involved in a cyberattack—either as the target or as a route to…

To Hell and Back: Recovering Active Directory During an Attack
- Semperis
What do you do when your endpoint or other initial protections are breached? When intruders are already in your network and have even compromised your Active Directory (AD) forest? This is the true story of a ransomware attack—and how it was stopped. Join Semperis’ Principal Technologist and MVP alumnus Guido…

Identity System Defense for the Healthcare Industry
- Semperis
Cyberattackers have healthcare systems in their sights. By breaching identity systems such as Active Directory and Entra ID, attackers can quickly compromise vital operational infrastructure and sensitive data throughout a healthcare organization. Securing the identity infrastructure is a key step in thwarting threat actors. Join Marty Momdjian, Semperis’ EVP of…
Snackable Active Directory Security: 30 Minutes a Day Keeps the Bad Guys Away
- Semperis
“I just don’t have the time to deal with Active Directory.” How many times have you heard (or said) that? Cleaning up years of AD configuration drift and tech debt can be a daunting task … but not as unpleasant as trying to recover the identity system after a full-blown…
Meine hybride Identität wurde gehackt — was nun?
- Semperis
Die Maxime "die IT von morgen ist hybrid" ist gängiger Standard in der IT-Beratung und bei Cloud-Anbietern. Auch Microsofts neue Sicherheits-Referenzarchitektur ist hybrid, betrachtet die Cloud als "Source of Security". Doch die Schattenseiten zeigen sich deutlich, wenn die hybride Identität kompromittiert wird. Dies bringt Herausforderungen wie Störungen beim Single Sign-On,…
Protect & Recover AD and Entra ID — The Keys to the Kingdom
- Semperis
In this on-demand webinar, Rob Ingenthron, Senior Solution Architect at Semperis, will delve into the significance of AD protection and recovery in identity threat detection and response (ITDR). Attendees can expect to: Discover effective strategies for integrating AD protection and recovery into a comprehensive ITDR approach. Gain a deeper understanding…
Are You Prepared for the True AD Disaster?
Explore the vital role of identity in disaster recovery planning, specifically focusing on Microsoft Active Directory. This on-demand webinar addresses the challenges in recovering core directory services and emphasizes the need for proactive planning. Key takeaways include reevaluating DR procedures, engaging with ITDR vendors, and enhancing identity security. The webinar…



