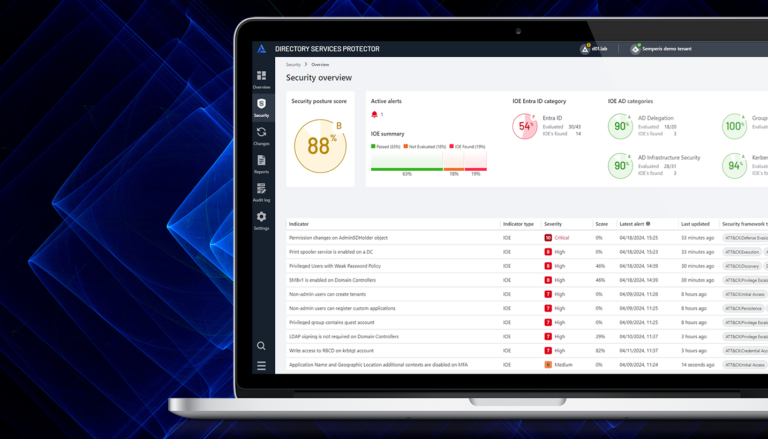
Lightning IRP captures, analyzes, and correlates authentication activities with Semperis’ identity threat intelligence to detect known attack patterns and signal malicious behavior.
- Password spray attacks: Monitors logon attempts to detect patterns indicative of a password spray attack
- Brute force attacks: Monitors repeated and rapid logon attempts against a single user to detect potential brute force attacks
- Anomalous logons: Looks for user logon anomalies that indicate an anomalous AD logon
- Anomalous resource access: Monitors a user’s activity and any interaction with services that indicate an attack on AD services
- Service ticket anomalies: Looks for suspicious service ticket requirements that indicate a Kerberoasting attack on AD