Active Directory Security
Categories
- Active Directory Backup & Recovery (67)
- Active Directory Security (231)
- AD Security 101 (17)
- Community Tools (25)
- Directory Modernization (9)
- From the Front Lines (69)
- Hybrid Identity Protection (76)
- Identity Attack Catalog (32)
- Identity Threat Detection & Response (161)
- Our Mission: Be a Force for Good (14)
- Purple Knight (5)
- Semperis University (5)
- The CISO's Perspective (16)
- Threat Research (77)
- Uncategorized (3)

Exploiting Ghost SPNs and Kerberos Reflection for SMB Server Privilege Elevation
- Andrea Pierini
- Oct 29, 2025
When misconfigured Service Principal Names (SPNs) and default permissions align, attackers can exploit Kerberos reflection to gain SYSTEM-level access remotely. Even with Microsoft’s security update, Ghost SPNs can still haunt you. Learn why.

Unlocking Unmatched Identity Resilience: The Semperis-Cohesity Partnership
- Chris Salzgeber | Product Manager, Integrations
- Sep 17, 2025
The Semperis-Cohesity partnership is the convergence of two industry leaders, each with singular expertise. With Cohesity Identity Resilience, organizations can be confident that their critical identity systems are secure and recoverable.
How to Secure Service Accounts: Protecting Identity Security’s Achilles’ Heel
- Ran Harel
- Jul 24, 2025
Securing service accounts is essential for identity system security, but in practice, it’s prohibitively time- and resource-intensive. Learn why service accounts are a stubborn security gap—and how to close it.
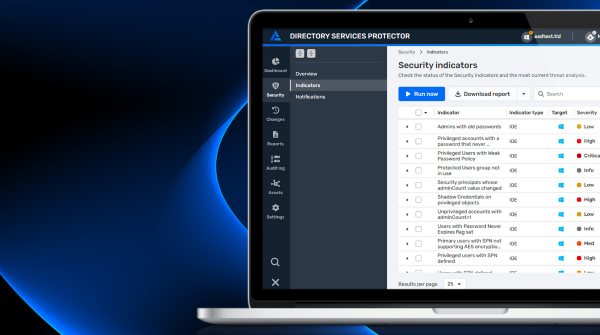
Improve Hybrid AD Security with Automated Response and Streamlined Administration
- Eran Gewurtz | Director of Product Management
- Jul 22, 2025
Service accounts are easy to misconfigure, hard to keep track of, and often forgotten, making them ideal entry points for cyber attackers. Learn how DSP expands your ability to discover, monitor, govern, and protect service accounts.

Golden dMSA: What Is dMSA Authentication Bypass?
- Adi Malyanker | Security Researcher
- Jul 16, 2025
Delegated Managed Service Accounts are designed to revolutionize service account management. But Semperis researchers have discovered a critical design flaw that attackers can exploit for persistence and privilege escalation in AD environments with dMSAs. Learn about Golden dMSA and its risks.

How to Block BadSuccessor: The Good, Bad, and Ugly of dMSA Migration
- Jorge de Almeida Pinto
- Jul 10, 2025
The BadSuccessor privilege escalation technique presents a severe risk to Active Directory environments that use delegated Managed Service Accounts. Learn how blocking dMSA migration prevents attackers from misusing a dMSA to take over an AD domain.

Understanding Identity Security Posture: See the Big Picture of Your Hybrid Environment
- Sean Deuby | Principal Technologist, Americas
- Jun 27, 2025
Pursuing cybersecurity maturity requires more than flipping a switch. To maintain a strong identity security posture, start by taking a broader look at the complex factors affecting your identity ecosystem.

How to Defend Against Password Guessing Attacks
- Daniel Petri | Senior Training Manager
- Jun 13, 2025
Here’s what you need to know about password guessing and how to protect Active Directory—and your organization.



