Webinar

Achieving Resilience: Strengthening Business Through Cyber Incident Preparedness
- Semperis
- Apr 30, 2025
In today’s threat landscape, attackers prioritize identity and access management systems like Microsoft’s Active Directory (AD) because they hold the keys to the kingdom in most enterprises. In other words, compromise AD, and you control the organization. That’s why modern cyber resilience strategies must focus on AD hardening, monitoring, and…
Tabletop to Reality: Building Cyber-Resilience Through Incident Response Drills
- Semperis
- Mar 16, 2025
In today's threat landscape, the speed and effectiveness of your incident response can mean the difference between a minor setback and a catastrophic breach. The question isn't if a cyberattack will happen, but when—and preparation remains your strongest line of defense. Tabletop exercises aren't just practice—they're essential in exposing vulnerabilities,…

Why Is Your AD an Easy Target for Hackers?
- Semperis
- Feb 28, 2025
Active Directory (AD) remains a cornerstone for many organizations, both on premises and integrated with Microsoft Entra ID in the cloud. Alarmingly, 90% of cyberattacks target AD, the central identity system for most enterprises. Semperis provides comprehensive protection for on-premises AD and Entra ID, offering continuous defense against identity-based threats before,…
Overcoming Vulnerabilities with Attack Surface Management
- Semperis
- Dec 30, 2024
As the digital landscape expands, managing and securing the attack surface of your organization has never been more crucial. Join us for a hot topics webcast where industry experts will provide a comprehensive forecast of attack surface management (ASM) trends and offer strategic guidance for late 2024 and early 2025.…
How to Recover Active Directory When Every Second Counts
- Semperis
- Dec 30, 2024
Microsoft Active Directory (AD) is a key target for cyberattackers. When AD goes down, so do your operations. Yet most organizations lack an AD-specific recovery plan or rely on manual recovery, which can take days if not weeks. Auditing your AD security stance and maintaining a solid incident response plan…
When Every Minute Counts Recovering AD During an Attack
- Semperis
- Dec 28, 2024
What do you do when your endpoint or other initial protections are breached? What do you do when intruders are already in your network and have possibly compromised your Active Directory (AD) forest? This is the true story of a ransomware attack—and how it was stopped. Join Semperis' Sean Deuby, 15-time…
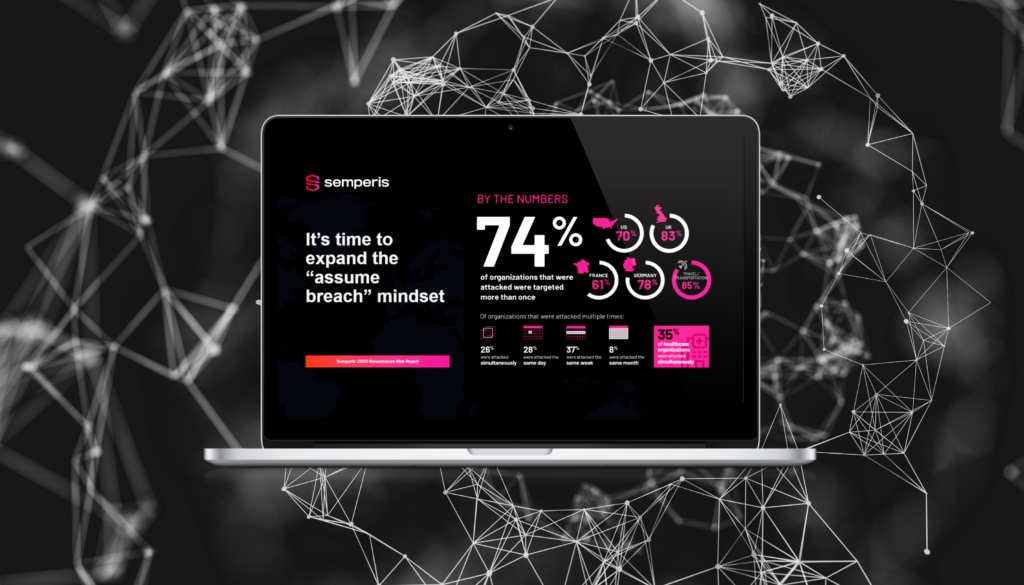
Business Continuity and Identity System Recovery
- Semperis
Is your disaster recovery plan designed with business continuity in mind? Unless it includes specific procedures for securely recovering Active Directory (AD) and Entra ID, you might be in for a nasty shock. Secure identity system recovery is a key factor in determining how quickly your organization can get back…
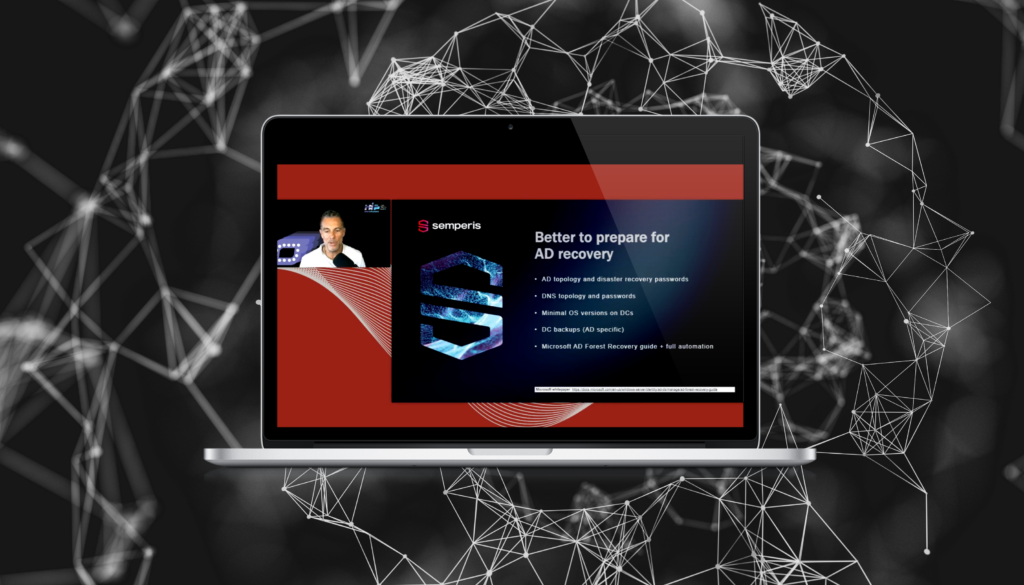
Recovering Operations After a Cyberattack
- Semperis
Critical infrastructure organizations that manage operational technology (OT) systems or Internet of Things (IoT) devices face several challenges to effective cybersecurity, including outdated technology, the complexity of diverse environments, and an increased attack surface. Rob Ingenthron (Senior Solutions Architect, Semperis) discusses the challenges faced by organizations in healthcare, manufacturing, energy…
Recovering Active Directory: The Missing Piece in Your Operational Resilience Plan
- Semperis
Ransomware and cybercrime have become top-tier threats to organizations in every industry. Securing endpoints, buying cyber insurance, even paying ransom—none of these options can prevent a business-ending attack. One step that is key to operational and business resilience: A dedicated, identity-first cybersecurity plan. Industry experts from Government Technology and Semperis…

Building a Layered Identity Defense
- Semperis
Cyberattackers are adept at finding ways through your defenses and into identity systems like Active Directory. From there, they can move laterally, escalate privileges, access sensitive resources, and inject malware or ransomware. Implementing a layered defense that includes identity threat detection and response (ITDR) is key to protecting your operational…



