Webinar
Top AI Attacks and How ITDR Can Prevent Them
- Semperis
- Nov 17, 2025
In this informative webinar, Semperis Chief Product Officer Alex Weinert explains how AI is enabling cyber attackers and how an effective ITDR strategy can help reduce attack impacts.
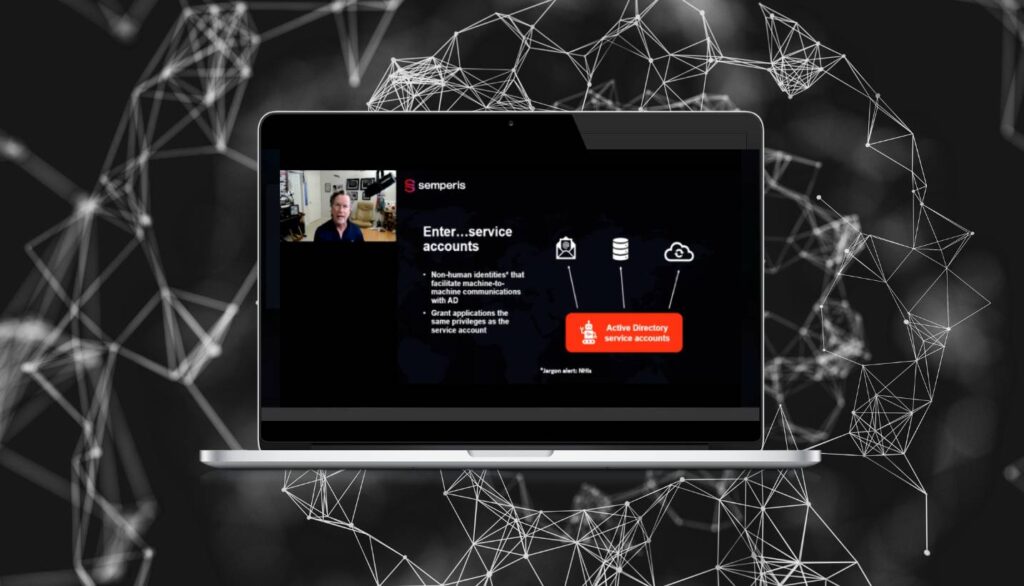
Mind the Gap: How to Secure Active Directory Service Accounts
- Semperis
- Nov 12, 2025
Service accounts are critical for enabling machine-to-machine communication in Active Directory (AD) environments. Email systems, databases, applications, even your security tools—all rely on service accounts for authentication. However, 94% of organizations lack full visibility into their service accounts. Learn how to close service account security gaps and strengthen IAM protection.
Como Recuperar o Active Directory Quando Cada Segundo Conta
- Oct 25, 2025
O Microsoft Active Directory (AD) continua sendo um dos principais alvos de ataques cibernéticos. Quando o AD é comprometido ou fica fora do ar, toda a operação da organização pode ser impactada. Ainda assim, muitas empresas não contam com um plano de recuperação específico para AD ou dependem de processos…
Defending the Public Sector: Confronting Cyber Threats with Limited Resources
- Semperis
- Oct 07, 2025
Public sector organizations are targets for today's most dangerous cyber adversaries, and resource and staffing shortfalls leave agencies vulnerable. Learn proven approaches to cyber crisis management and resilience that can help you close security gaps.
Resilience in the Crosshairs: Best Practices for Securing Identity Systems Against Modern Threats
- Semperis
- Aug 18, 2025
Today's threat actors aren't just evolving—they're organizing. From ransomware gangs mimicking corporate structures to nation-state threats targeting critical infrastructure, security teams are facing an unrelenting wave of identity-based attacks. At the center of this onslaught is Active Directory (AD)—still the most common target for lateral movement and privilege escalation. In…

Using Lighting Intelligence for Continuous Saas Identity Security Assessment
- Semperis
- Jul 31, 2025
Lightning Intelligence is an easy-to-deploy SaaS security posture assessment tool for AD and Entra ID that automates identity environment scanning so you won’t miss emerging threats. In this video, Tammy Mindel, product owner of Purple Knight and Lightning Intelligence at Semperis, takes you for a tour of Lightning Intelligence: Learn…
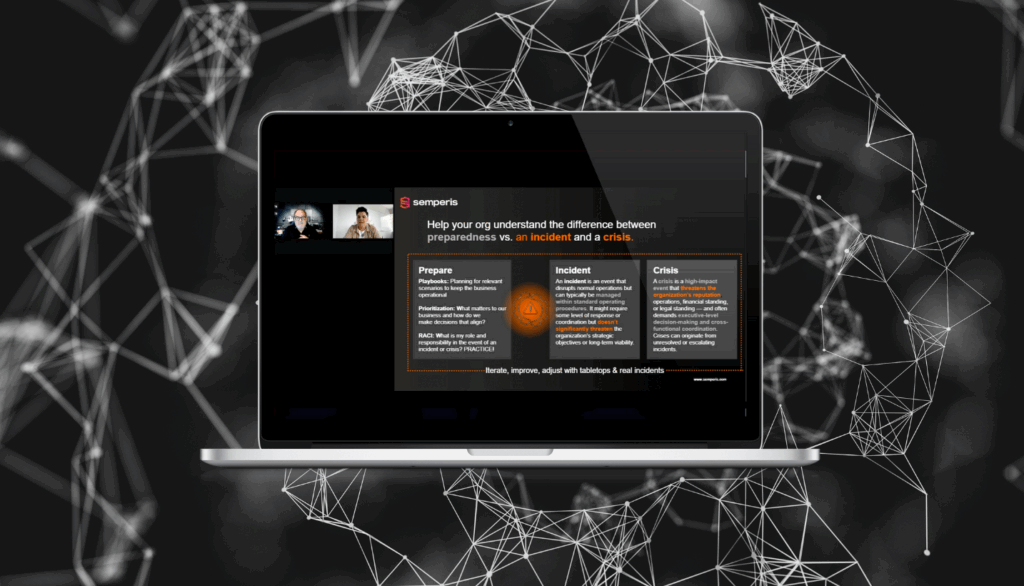
Tech Talk — From Chaos to Control: Rethinking Cyber Crisis Management
- Semperis
- Jun 26, 2025
In today’s digital world, cyber incidents aren’t just IT issues—they’re full-blown business crises. Although many organizations have incident response plans in place, those plans often collapse under the pressure of a real-world event. In this webinar, Courtney Guss (Director of Crisis Management, Semperis) shares why traditional approaches to crisis management…
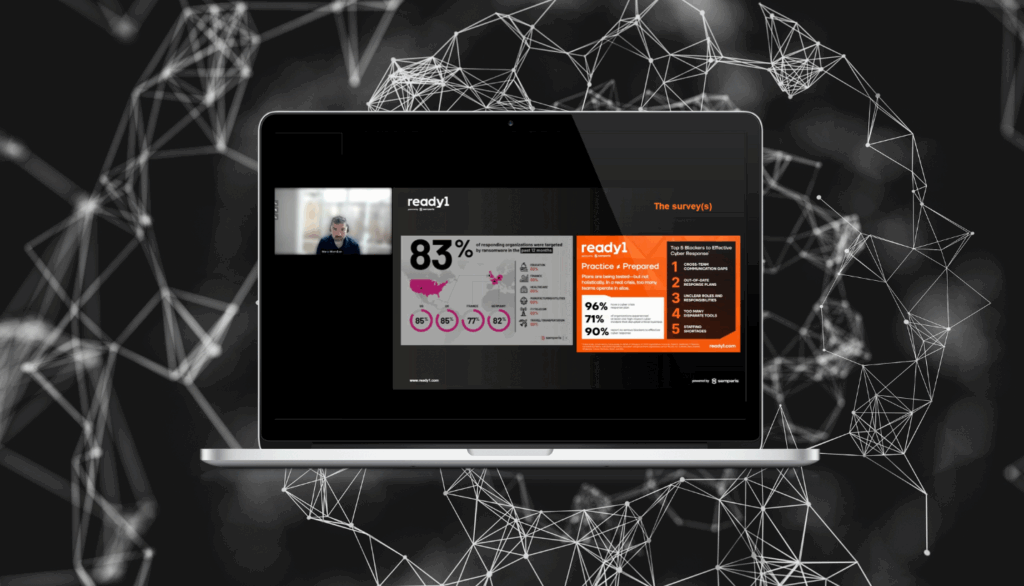
Cyber Resilience By Design
- Semperis
- Jun 13, 2025
Healthcare is a high-value target for threat actors and adversaries. Yet all too often, incident response plans rely on assumptions that can fall apart during a real crisis. In this focused webinar, you’ll learn why healthcare has a “cyber-crisis management crisis” and how organizations can achieve cyber and operational resilience.…
Beyond Defense: Active Directory Recovery and Business Resilience
- Semperis
- May 19, 2025
Endpoint security, cyber insurance, and generalized disaster recovery plans are all important—but they won’t save your business from a major cyberattack. To keep operations running smoothly despite cyber threats, analysts and cybersecurity leaders recommend a focus on resilience. In this session, James Ravenell (Senior Solutions Architect, Semperis) explains why the…
Closing the Gap for Government Agencies: 5 Ways to Automate Cyber Resilience
- Semperis
- May 19, 2025
Operational continuity depends on cyber resilience. Maintaining that resilience can be tricky when resources are scarce. Attackers know this and are skilled at turning staffing turnover and technology gaps to their advantage. Attackers’ favorite means of spreading malware, escalating privilege, and establishing perseverance is the identity infrastructure—typically Microsoft Active Directory…



