Ransomware Targets Times of Distraction
Most ransomware attacks occur when organizations reduce staffing or after material corporate events.
When do most ransomware attacks occur?
As noted in the Semperis 2025 Ransomware Risk Report, this year’s study showed an overall drop in the frequency of ransomware attacks overall. Still, more than half of global study respondents who reported being targeted said that the attack occurred during a weekend or holiday. And even more said that they were attacked after a material corporate event, such as a merger or acquisition.
Get the report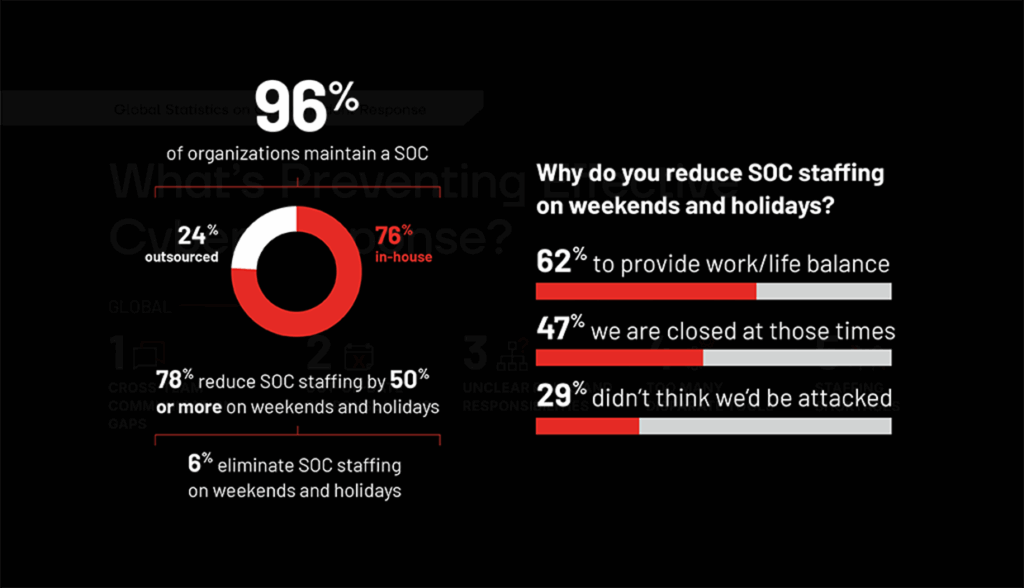
What do SOC leaders need to know?
We are encouraged to see a slight rise in the share of companies that say they staff their SOC at more than half-capacity during weekend and holiday periods. Unfortunately, more than three-quarters still cut SOC staffing by 50% or more at those times … and some do not staff their SOC at all outside of the regular workweek.
of global companies scale back on their after-hours SOC staffing levels by 50% or more
of respondents said their SOC is not staffed at all during holidays or weekends
Can your identity infrastructure stand up to ransomware?
ITDR strategy adoption increased slightly this year, to 90%. Nearly all those who said they have an ITDR plan also said that they have procedures in place to scan for identity system vulnerabilities. However, many organizations lack procedures and plans to remediate vulnerabilities and to recover identity systems after an attack.
Get the reportMore resources
Learn more about how to prevent, detect, and respond to identity-based attacks.