Keeping Active Directory (AD) secure is a never-ending challenge. Between attackers trying to gain domain dominance and admins making unintentional misconfigurations, unwanted changes happen all the time.
That’s where Directory Services Protector (DSP) comes in. One of its most useful features is Auto Undo, which automatically rolls back specific changes to critical AD objects without requiring manual intervention. This is a big deal because it means you can reverse unauthorized modifications whether they’re caused by an attacker, a rogue admin, or just human error.
In this blog post, you’ll learn why Auto Undo is useful and how it works and explore some real-world scenarios where it makes a difference.
Why is automated rollback useful for protecting AD from risky changes?
Most AD modifications are routine. But some changes should almost never happen under normal circumstances.
For example, adding a user to legacy groups like Account Operators, Backup Operators, Print Operators, or Server Operators is a red flag. These groups were intended for older administrative models and should remain empty in modern environments. Even if they’re unintended, such changes can introduce serious security risks.
For most organizations, manually monitoring and rolling back every risky change isn’t practical—or even possible. Automating change auditing and rollbacks is essential to protect sensitive AD and Entra ID objects and attributes.
How does Auto Undo work to automate AD change rollbacks?
Auto Undo is an automated rollback mechanism that reverts unwanted AD changes, whether they stem from a security threat, an unauthorized modification, or an admin mistake.
DSP detects changes to AD in real time. When you enable the Auto Undo feature instead of relying on manual intervention, DSP restores the original state before the change can cause any harm.
You enable the feature through rules that automate change rollback for specific operations: Modify, Add, Move, and Remove. And DSP notifies you of changes that are automatically reverted.
Let’s take a closer look at how Auto Undo works.
Auto Undo in Action: Protecting AdminSDHolder
Modifying the security descriptor of the AdminSDHolder container can have serious security implications, as it controls protected accounts and groups. Such changes often indicate misconfigurations or potential abuse and should be detected and reverted immediately to prevent privilege escalation or other unintended security risks.
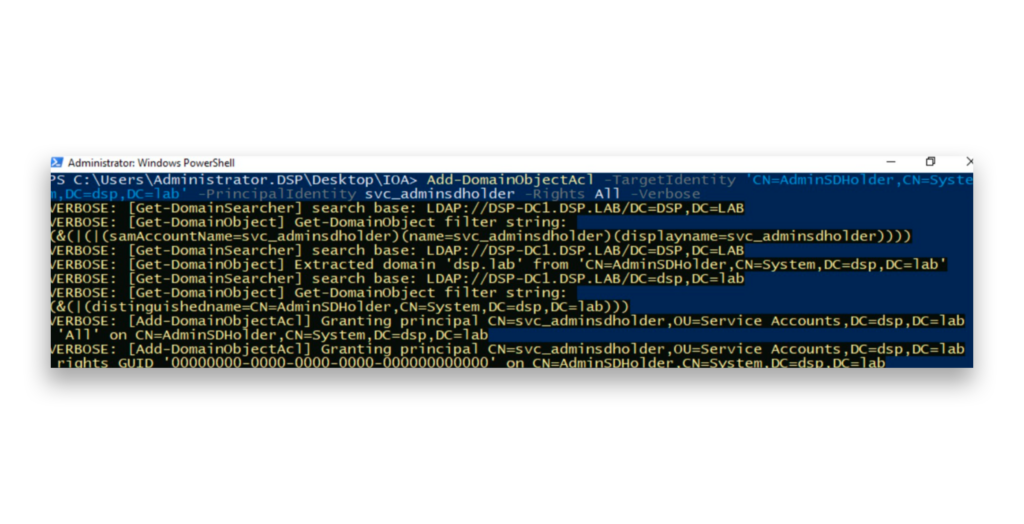
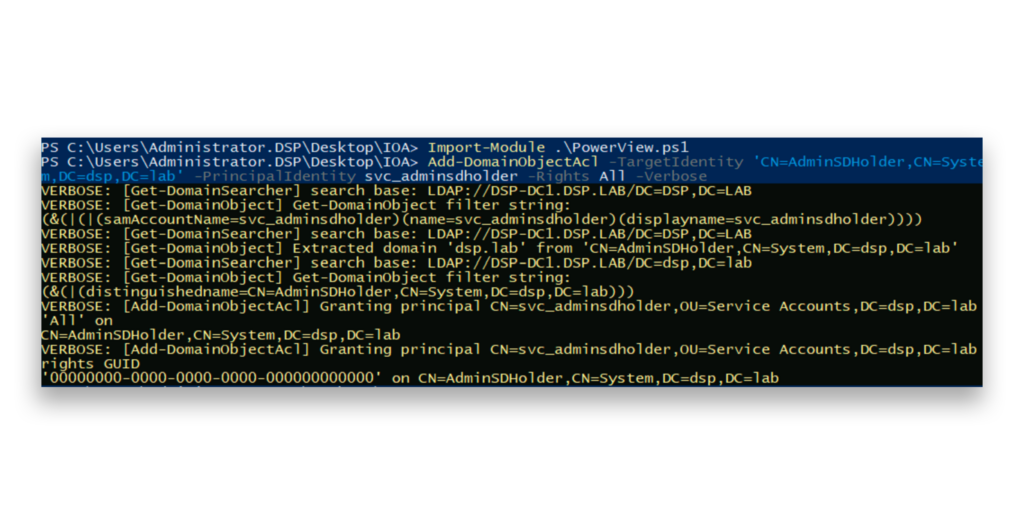
As a demonstration, we will modify the security descriptor of the AdminSDHolder container to grant a specific account full control (Figure 1).
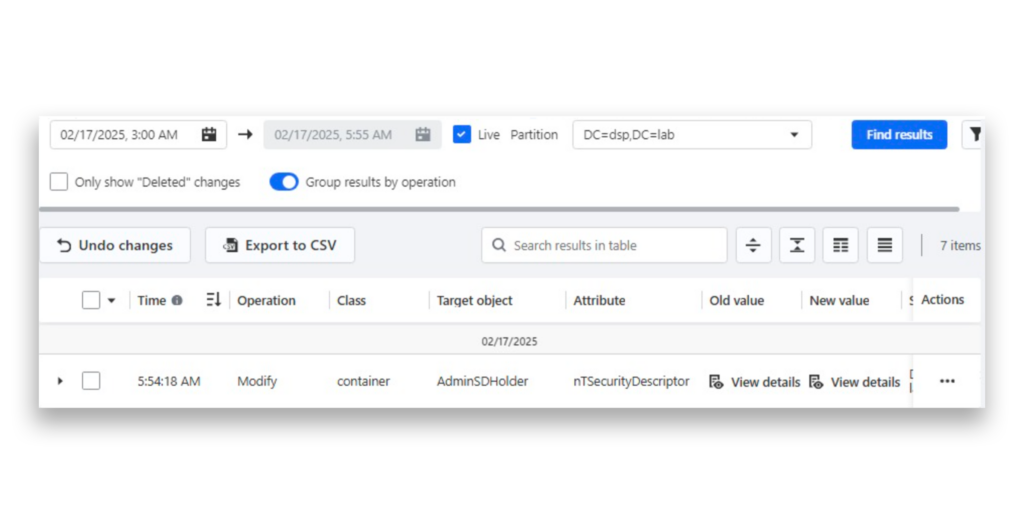
After we complete our modification, an entry appears in the AD Changes section in DSP, showing that this container was modified. Specifically, the nTSecurityDescriptor attribute reflects the changes made to its permissions (Figure 2).
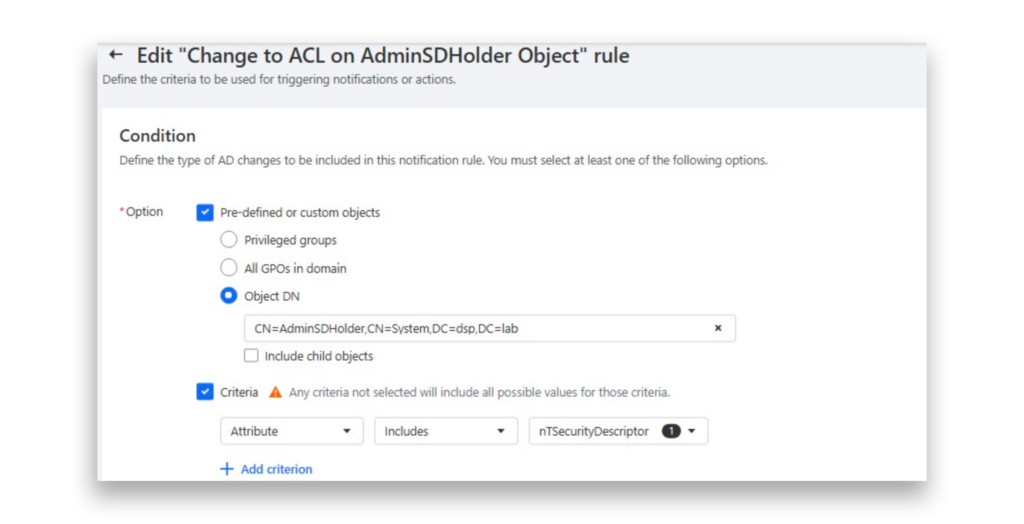
DSP enables you to set up notification rules and receive email alerts whenever a specific AD change occurs. In the example that Figure 3 shows, we configured a rule to trigger an email notification whenever the permissions of the AdminSDHolder container are modified.
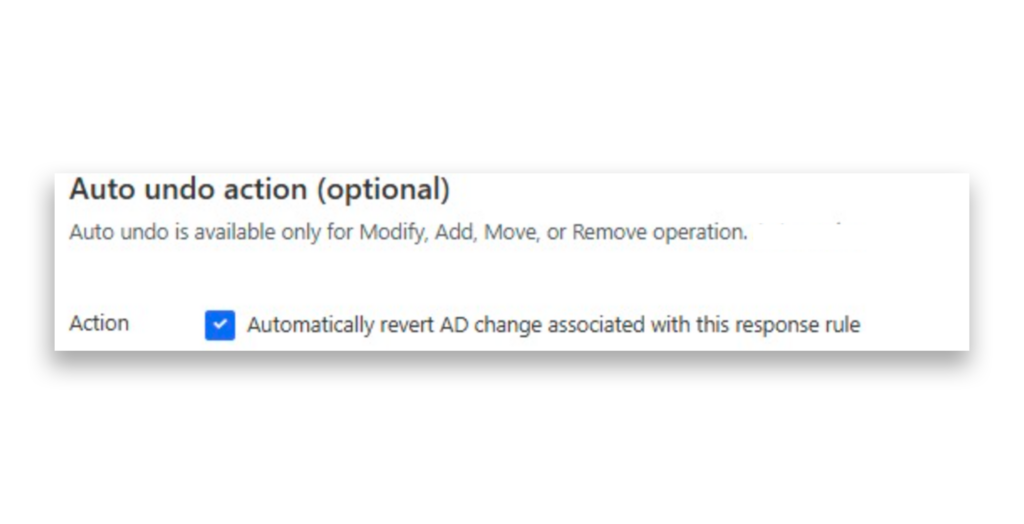
In the notification rules, you can set up an auto undo action so that whenever the rule is triggered, the AD change is automatically reverted (Figure 4).
Now, let’s try changing the AdminSDHolder again by granting permissions to a specific account, GenericAll (Figure 5). What will happen this time?
As Figure 6 shows, when we review AD Changes now, we see two entries indicating that the nTSecurityDescriptor was modified on the AdminSDHolder container.
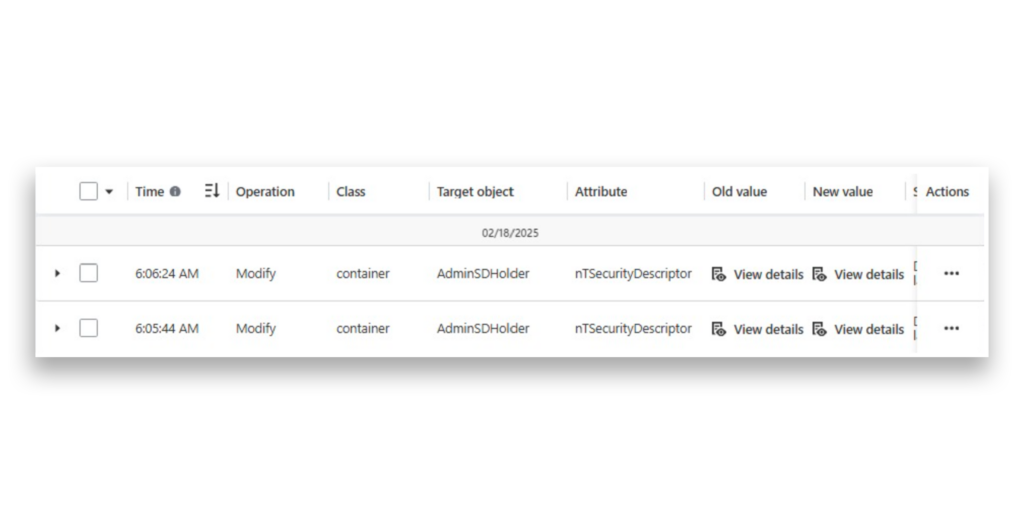
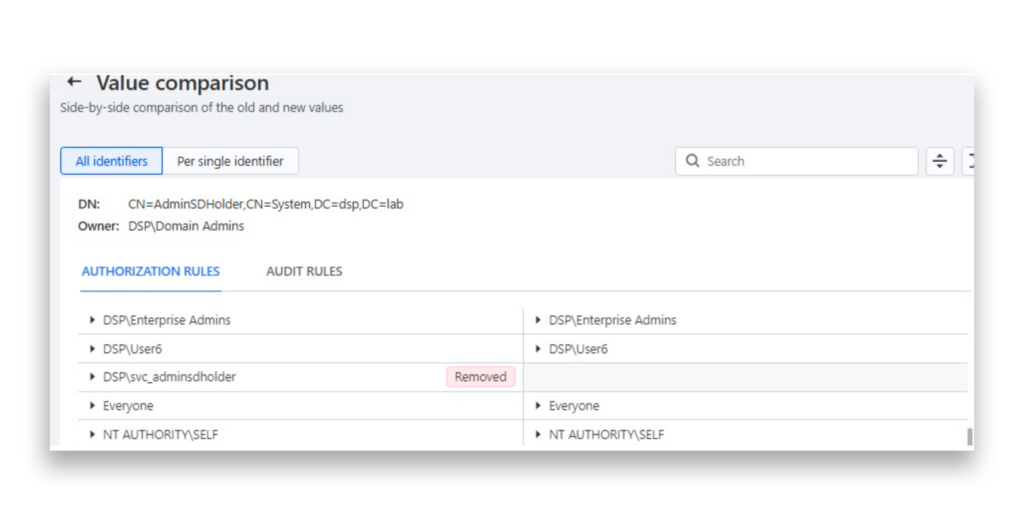
The most recent modification entry is the Auto Undo action. DSP has automatically removed the permissions from the specified account, as Figure 7 shows.
Auto Undo in action: Preventing Unconstrained delegation
Configuring a server for unconstrained delegation means that any account that requests a service ticket from the server will have its Kerberos Ticket Granting Ticket (TGT) exposed in memory. This exposure can include highly privileged accounts like Domain Admins.
A well-known attack exploits unconstrained delegation by using the Print Spooler service. In this approach, an attacker forces a domain controller (DC) machine account to authenticate to a compromised server configured for unconstrained delegation. If the Print Spooler service is enabled on the DC, the DC’s TGT will be exposed in memory on the attacker-controlled server. With access to the DC’s TGT, the attacker can impersonate the DC itself. In short, unconstrained delegation should never be enabled as it introduces significant security risks.
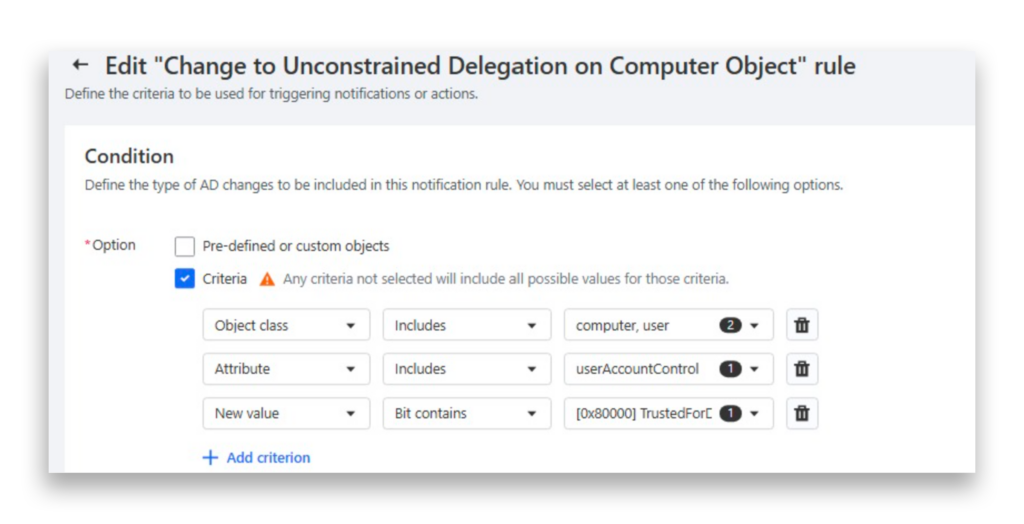
Let’s set up a notification rule with an auto undo action to revert any instance where a user or computer object is configured for unconstrained delegation (Figure 8).
To test the rule, let’s enable unconstrained delegation on a specific server (Figure 9). This will configure the server to accept delegation requests for any service—meaning any account that requests a service ticket from it will have its TGT exposed in memory.
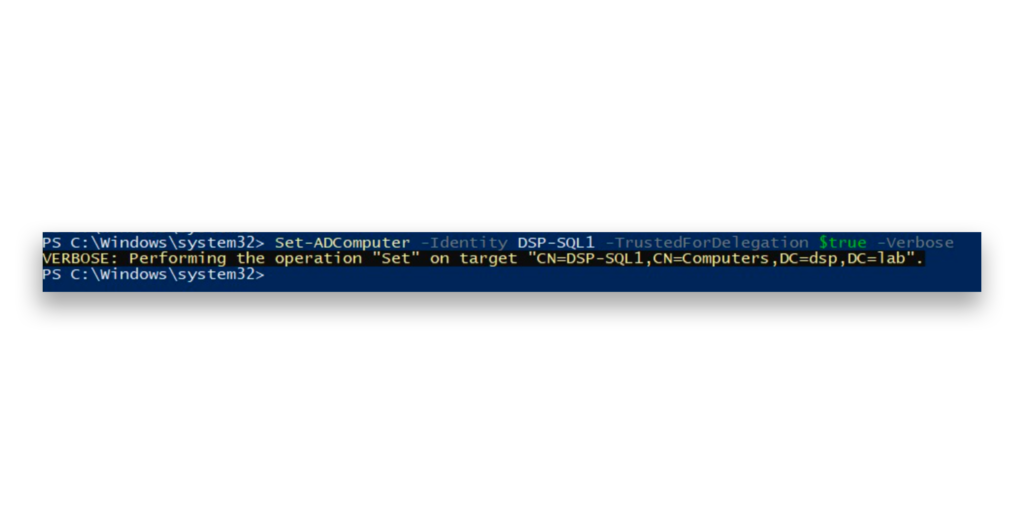
Now, you can see that two entries have appeared in AD Changes, indicating that the userAccountControl attribute has been modified (Figure 10).
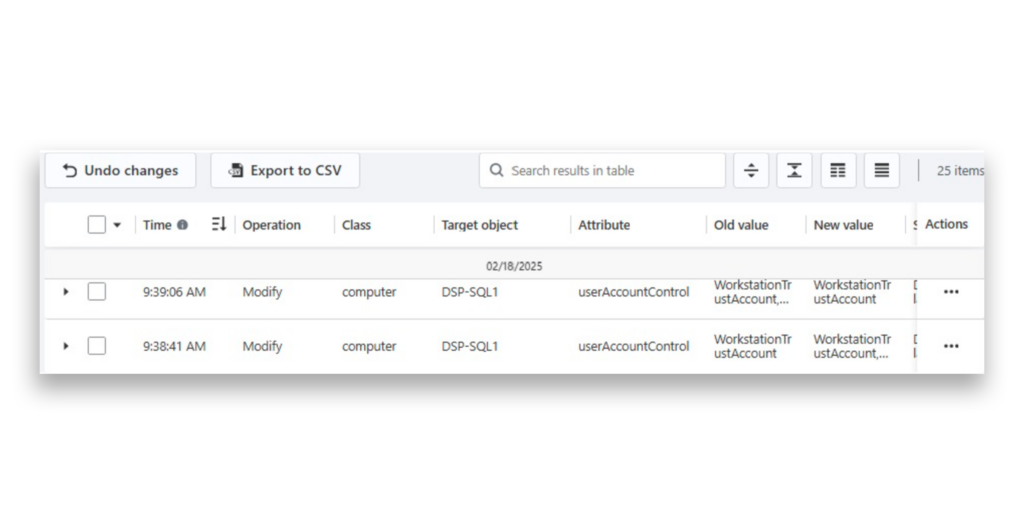
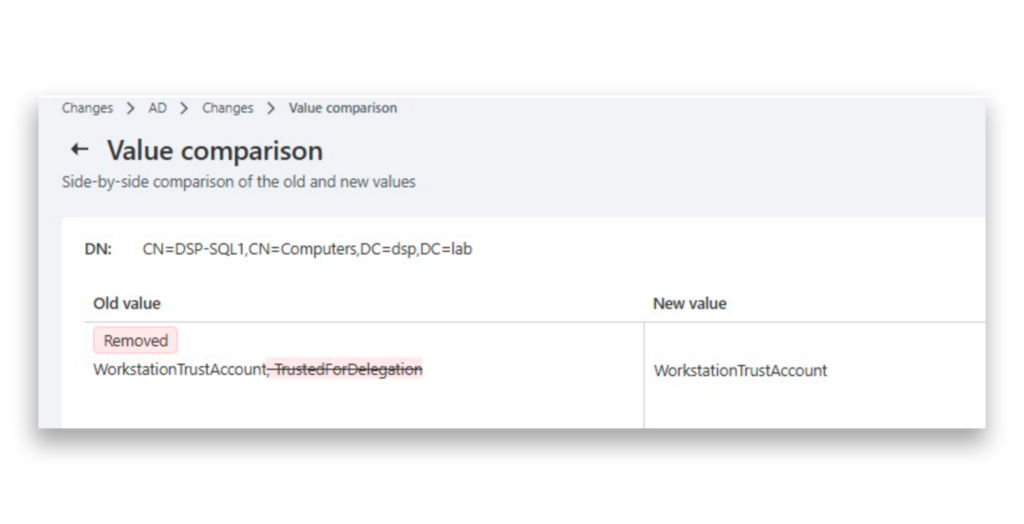
The latest DSP change, where the userAccountControl attribute was modified on this server, indicates that the auto undo rule successfully reverted the change back to its previous state automatically (Figure 11).
Semperis snapshot
Auto Undo is a practical way to keep Active Directory secure by automatically reversing changes that shouldn’t happen. Instead of waiting for someone to notice and fix a misconfiguration, it steps in immediately to prevent potential security risks.
This feature is especially useful for preventing changes to critical attributes such as AdminSDHolder and unconstrained delegation, where bad actors can rapidly do significant damage. With Auto Undo in place, admins don’t have to constantly monitor for these issues because DSP takes care of them automatically.
Learn more about Active Directory security
- Active Directory Change Auditing & Rollback
- Directory Services Protector
- Improving Your Active Directory Security Posture: AdminSDHolder to the Rescue
- Unconstrained Delegation in Active Directory
- Unconstrained Delegation Explained
- What You Need to Know About the Critical Windows Print Spooler Vulnerability
