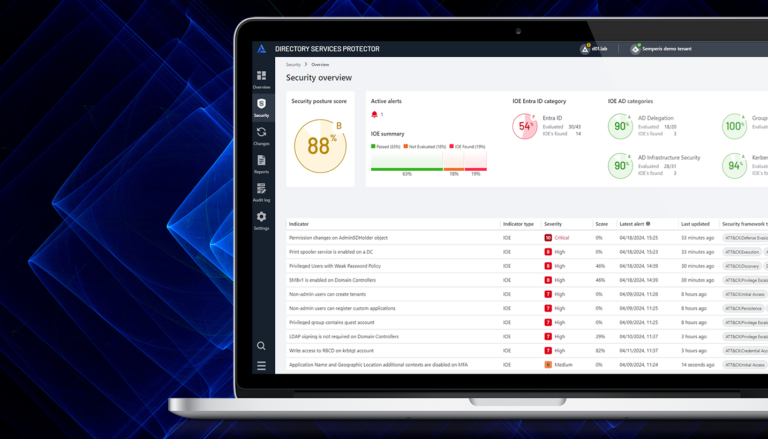
Service Accounts Protection
Discover dormant and unmanaged service accounts, continuously detect misuse, and receive alerts on malicious service account behavior with Service Accounts Protection in Directory Services Protector.
Gain control of your service accounts in Active Directory
Service accounts are critical to enterprise IT operations—integrating Active Directory with email, databases, and other applications and services. Not only are service accounts essential to business operations, they also are notoriously difficult to secure: 94% of organizations do not have full visibility into their service accounts, according to Security Magazine.
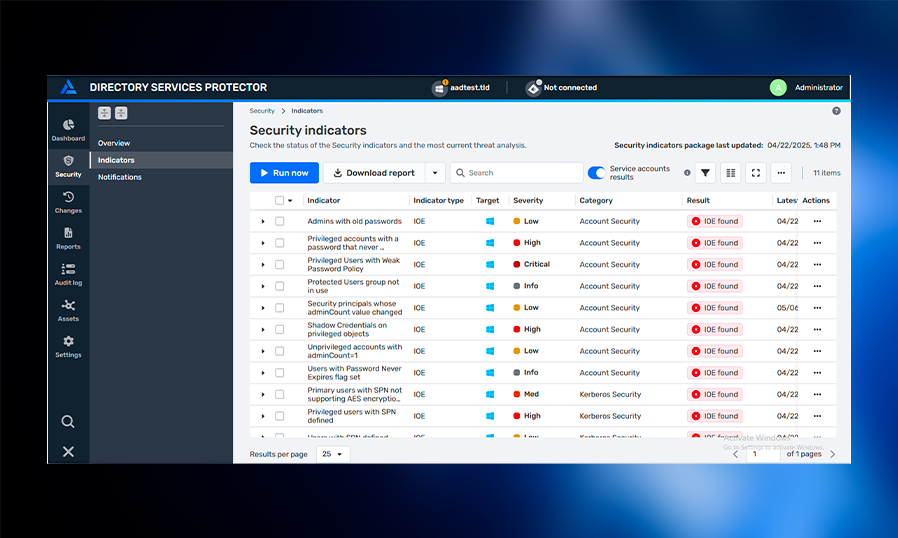
Reduce risk with complete visibility and centralized control over service accounts
Directory Services Protector with Service Accounts Protection provides complete visibility into your Active Directory service account posture. Discover dormant and misplaced service accounts, manage service account risk, uncover excessive permissions, detect risky configurations, and receive alerts on malicious service account behavior.
Frequently asked questions about Service Accounts Protection
Service accounts are a form of non-human identity that facilitate machine-to-machine communications to AD. For example, email platforms, databases, and internal and internet-facing applications rely on these types of accounts to integrate with AD.
Low visibility: Many Active Directory environments have been in place for years, accumulating service accounts from countless onboarded and retired applications. These accounts often remain active long after their associated apps are gone, leading to hundreds or thousands of stale entries. Traditional logging methods struggle to track service account behavior and detect malicious usage, further complicating efforts to identify and retire unused accounts.
Excessive privileges: Service accounts often have excessive privileges because application developers often require more privileges than necessary for the application or service to function, including administrative access.
Static passwords and no MFA: Service accounts often rely on static passwords that rarely change and are sometimes hard-coded into scripts or applications, making them difficult to update. Since these accounts aren’t tied to a person, they can’t use MFA, leaving them without a critical layer of protection and vulnerable to credential theft attacks.
Business criticality: When a service account loses access to AD or Entra ID because of a lockout, password change, or other issue, the associated application might stop functioning. Because these accounts often support essential services like email or databases, administrators are often reluctant to make changes that could risk downtime or disrupt business operations.
Service Accounts Protection Essential enhances Directory Services Protector’s hybrid AD threat detection and response by:
- Providing complete centralized visibility into all service accounts, their permissions, and usage
- Continuously monitoring service account security posture, including excessive permissions, risky service account passwords, and anomalous logons
- Reducing attack surface by discovering dormant and stale service accounts
- Detecting malicious behavior and stopping service account misuse at scale with automatic rollback
Save time detecting and responding to identity-based attacks
More resources
Learn more about how to prevent, detect, and respond to identity-based attacks.