Despite widespread cybersecurity efforts, many organizations are unintentionally opening a door to ransomware by reducing their defenses during weekends and holidays. Attackers clearly expect this risky behavior and target these periods — as well as other material corporate events that might signal distracted or reduced defenses — to strike. This report includes:
- Expert guidance for strengthening ransomware defense, especially during high-risk periods such as holidays, weekends, and corporate transitions
- Insights into ransomware attack patterns from a survey of 900 IT and security leaders, revealing that many organizations lack adequate defenses against attacks that strike during times of distraction
- New evidence that organizations routinely overestimate their ability to defend against identity-based attacks
We must assume an ever-present state of threat. This is not just the notorious cases that we hear about every quarter or so. This is happening all day, every day, to a range of companies.
Chris Inglis, former US National Cyber Director, former Deputy Director of the NSA, Semperis Strategic Advisor
Executive Summary
Ransomware attacks don’t observe business hours, and attacks often move too quickly for human intervention alone. Therefore, automated identity playbooks are required to mitigate risk.
Threat actors strike during periods of absence or distraction, such as holidays, weekends, and corporate events, including mergers and acquisitions.
Organizations across the globe are locked in a battle against ransomware and cyberattacks. As the stakes increase, so does the evidence that Microsoft Active Directory is a top target for threat actors and that identity threat detection and response (ITDR) is a key aspect of both cyber and operational resilience.
To examine trends in ransomware’s frequency, severity, and impact, Semperis partnered with international research firm Censuswide to conduct a comprehensive study spanning multiple industries across the United States, the United Kingdom, France, and Germany. The first report of our findings—2024 Ransomware Risk Report—revealed that ransomware attacks are incessant and costly. Now, our second report—2024 Ransomware Holiday Risk Report—examines the timing of attacks that occur during periods of corporate distraction (including holidays, weekends, and material events such as mergers, IPOs, and layoffs) and potential gaps in organizations’ cybersecurity defenses.

Contributing Experts
Mickey Bresman, Semperis CEO
Sean Deuby, Semperis Principal Technologist (North America)
Guido Grillenmeier, Semperis Principal Technologist (EMEA)
Simon Hodgkinson, Semperis Strategic Advisor, former bp CISO
Chris Inglis, Semperis Strategic Advisor, former US National Cyber Director
Ciaran Martin, CB, Paladin Capital Group Managing Director, founding Chief Executive of the UK’s National Cyber Security Centre
Kemba Walden, Paladin Global Institute President, former Acting US National Cyber Director
Jeff Wichman, Semperis Director of Incident Response
Ransomware attackers strike when security coverage is lighter or when companies are distracted.
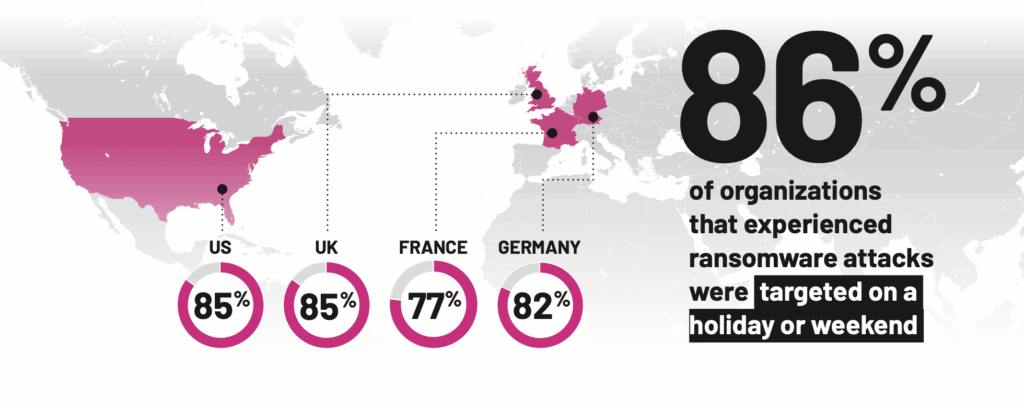
Attackers Don’t Take Holidays
“When attackers get inside a company’s systems, especially if it’s on a holiday weekend when staff is diminished, they may not be noticed right away. Companies are less careful and more vulnerable during those periods, and attackers know that.”
Guido Grillenmeier Principal Technologist (EMEA), Semperis
Attackers Strike When SOC Staffing Is Reduced
Ransomware threats demand 24/7/365 attention. Most of the organizations included in our study (96%) said their SOC operates 24/7/365, through some combination of internal and external resources. Even so, the majority of global companies (85%) scale back on their after-hours SOC staffing levels by up to 50%. And alarmingly, nearly 5% of respondents indicated that their SOC is not staffed at all during holidays or weekends. Organizations that scaled back SOC staffing during holidays and weekends did so for multiple reasons:
- They did not think it was necessary, considering most employees work only during weekdays or their business was open only Monday through Friday.
- Their business had never been targeted by ransomware, or they did not believe that it would be targeted.
- They were attempting to maintain a work-life balance for staff.
Attacks Occur During Times of Corporate Distraction
Leadership and staff changes, system integrations, and mergers create vulnerabilities. Times of corporate upheaval—whether a merger, acquisition, IPO, or reduction in workforce—are also magnets for ransomware attackers. Semperis survey data show that the majority (63%) of respondents also experienced a ransomware attack following a material corporate event. Not only do these situations create the distractions that bad actors love to exploit, but attackers can often extract large ransoms from companies desperate to regain access to critical systems or prove operational competence ahead of a major transaction. In addition, such events create inherent identity security challenges.
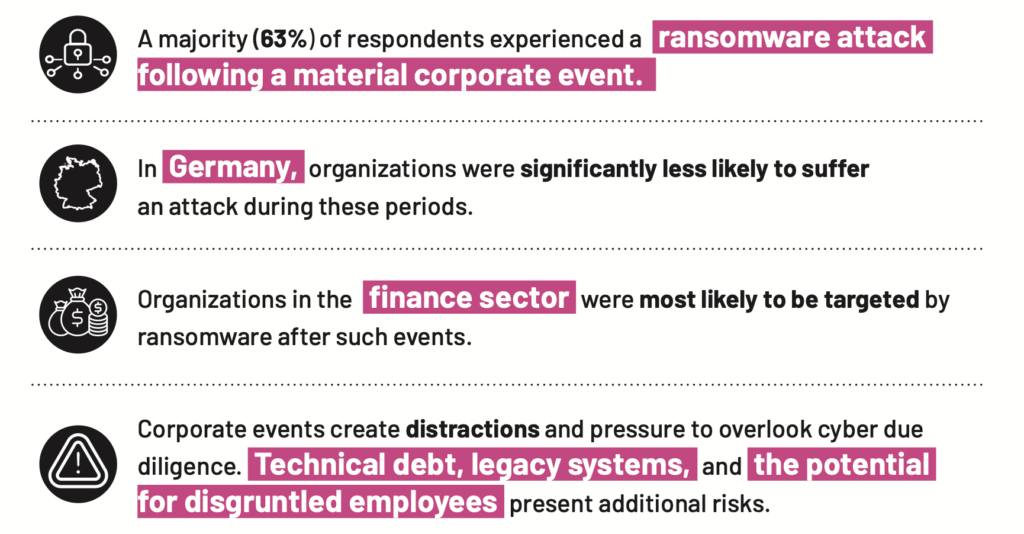
Identity Protection Is Pivotal to Business Resilience
Operational resilience depends on strong Active Directory security and a dedicated identity system recovery plan. Whether for financial or cultural reasons, organizations are facing a clear gap in their cyber defenses. Fully staffing a 24/7/365 SOC might help to close this gap, as would increasing IT and security resources immediately before, during, and after material corporate events. Realistically, such an increase in staffing might be difficult to achieve. Yet organizations must take steps to strengthen their ransomware defenses during these critical periods.
Aligning Business Priorities
Elevating cybersecurity to a business priority and implementing automated monitoring solutions will help organizations protect themselves against ransomware risk.
Ransomware attacks can, and do, strike when least expected. No company—regardless of region, sector, or SOC status—should underestimate the need for constant vigilance. Furthermore, cybersecurity leaders are increasingly insistent that successful ransomware defense efforts must include a clear plan to defend and recover Active Directory.
So, what steps can business, technology, and security leaders take to reduce the likelihood of a successful ransomware attack and increase their ability to say “no” to threat actors? Our experts suggest three initial actions.
- STEP 1 C-level leadership must acknowledge ransomware defense and identity security as business priorities.
- STEP 2 Robust ITDR solutions and expert partners can help security leaders offset staffing challenges.
- STEP 3 Active Directory security should be a core aspect of every merger or acquisition.
KEY TAKEAWAYS
- Ransomware and identity defense are no longer simply IT challenges; they are business priorities.
- Expert ITDR solutions can help to automate ransomware detection and defense in the face of staffing challenges.
- Active Directory security auditing is a necessary part of due diligence in advance of material corporate events.
“Improving operational resilience during material events takes patience and diligence. It is essential that the CISOs at both organizations involved in the material event connect prior to any deal and discuss ‘must haves’ from a security standpoint before the integration of networks begins. They should also identify vulnerabilities and weak spots and make sure both organizations have the best resources available to reduce risks.”
Kemba Walden, Paladin Global Institute President, former Acting US National Cyber Director
