For cyberattackers, gaining access to the identity system is just the start of their journey into your organization. Once they’ve leveraged any of dozens of attack techniques to get in, they want to maintain their presence and evade detection while escalating privileges, moving laterally through your organization, and gathering vital information along the way.
To aid penetration testers and security teams in detecting and preventing cyberattacks, a variety of post-exploitation tools are available—including a new tool specifically designed for Active Directory (AD) environments: Cable.
Although post-exploitation tools are made available to aid learning and development of defense strategies, they can be used by attackers as well. So, in this article, we’ll explore how to defend against a malicious actor using Cable.
What is the Cable post-exploitation tool?
Cable is a post-exploitation tool written in .NET that’s used to interact with AD. It allows operators to enumerate users, groups, computers, trusts, and certificate authorities, as well as modify permissions on AD objects. As Figure 1 shows, Cable modules support actions like setting Service Principle Names (SPNs), managing group memberships, and exploiting resource-based constrained delegation (RBCD).
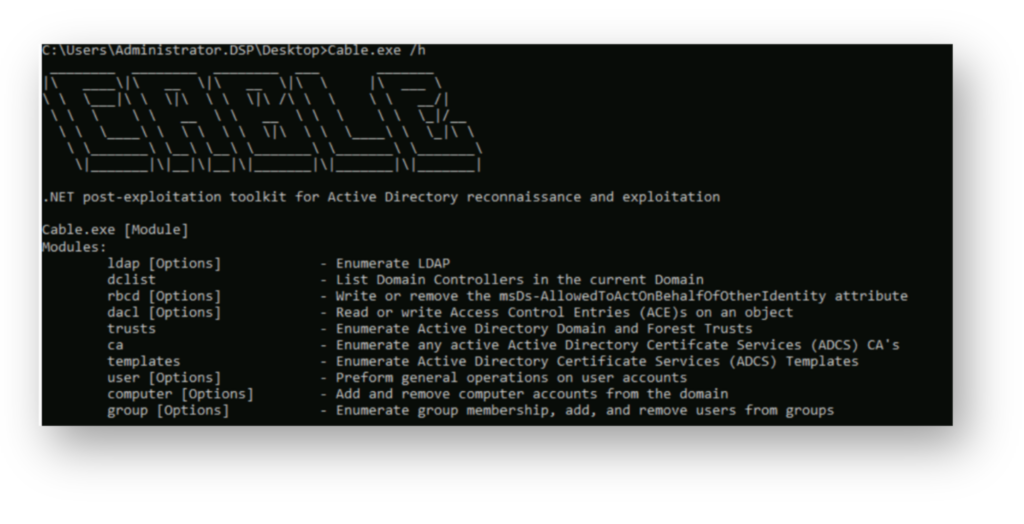
Figure 2 shows the available options under Cable’s ldap module, which focuses on querying Active Directory objects. It supports enumeration of users, computers, and groups, as well as more targeted searches like accounts with SPNs, unconstrained delegation, or adminCount set to 1. These options are useful for identifying accounts that may be misconfigured or pose a higher risk—or an opportunity, from an attacker’s perspective.
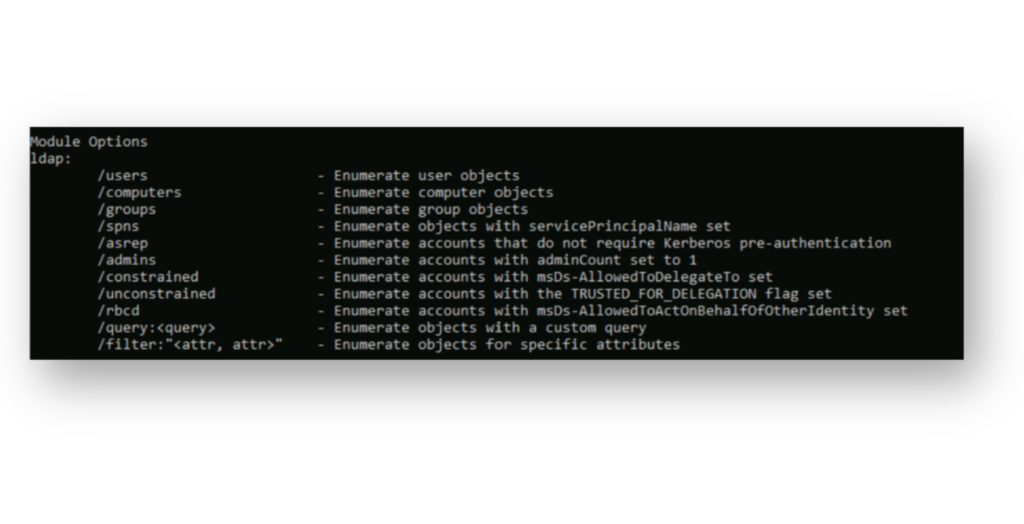
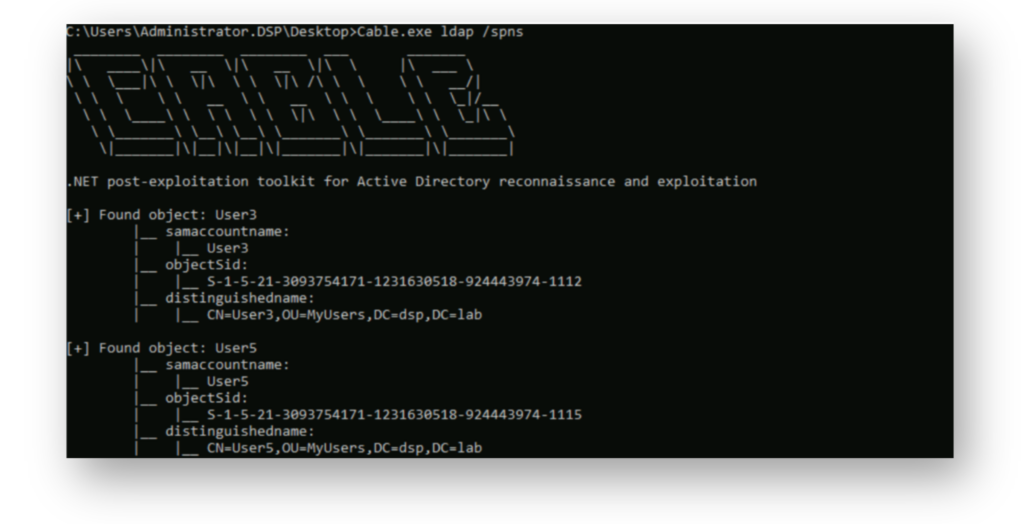
ldap module in Cable offers a variety of options to enumerate key AD objects and identify accounts with interesting attributes like SPNs, unconstrained delegation, or missing Kerberos pre-auth.For example, using Cable’s /spns option (Figure 3) allows you to enumerate accounts with an SPN configured, which is a common step in Kerberoasting attacks. These accounts can be targeted by requesting a service ticket, which can then be brute-forced offline to try and recover the password.
How to defend against Cable
Cable uses LDAP queries to identify specific weaknesses in Active Directory, such as servers with unconstrained delegation, accounts without Kerberos pre-authentication, accounts vulnerable to Kerberoasting, and more.
Both Semperis Directory Services Protector (DSP) (Figure 4) and our free community tool, Purple Knight, also scan for AD weaknesses—including the specific issues that the Cable tool targets.
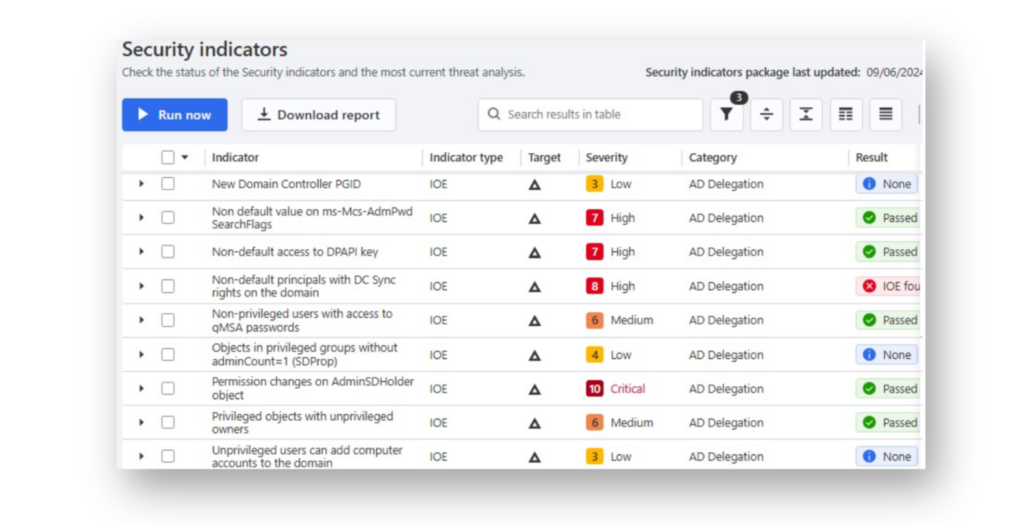
For example, as we can see in Figure 5, DSP includes several indicators of exposure (IOEs) that detect risks related to SPNs.
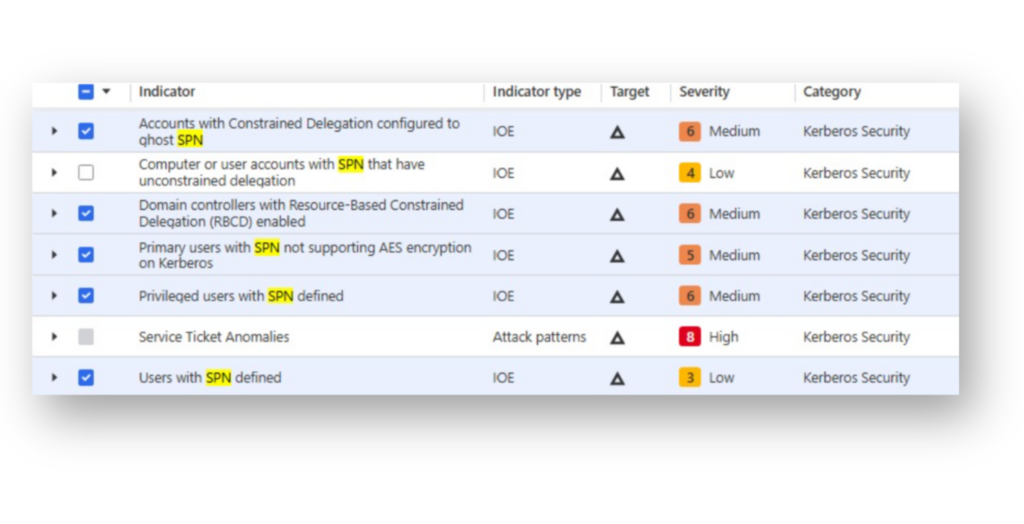
Example: Detecting Cable use in AD
A common attack method, Enterprise CA Security Configuration (ESC1), involves Active Directory Certificate Services (AD CS), where misconfigured or overly permissive certificate templates can be abused to escalate privileges to Domain Admin or equivalent.
For example, during reconnaissance, an attacker might discover that Domain Computers have enrollment rights to a certificate template configured with the ENROLLEE_SUPPLIES_SUBJECT flag and the Client Authentication EKU (Figure 6), which is a combination that can open a path for privilege escalation.
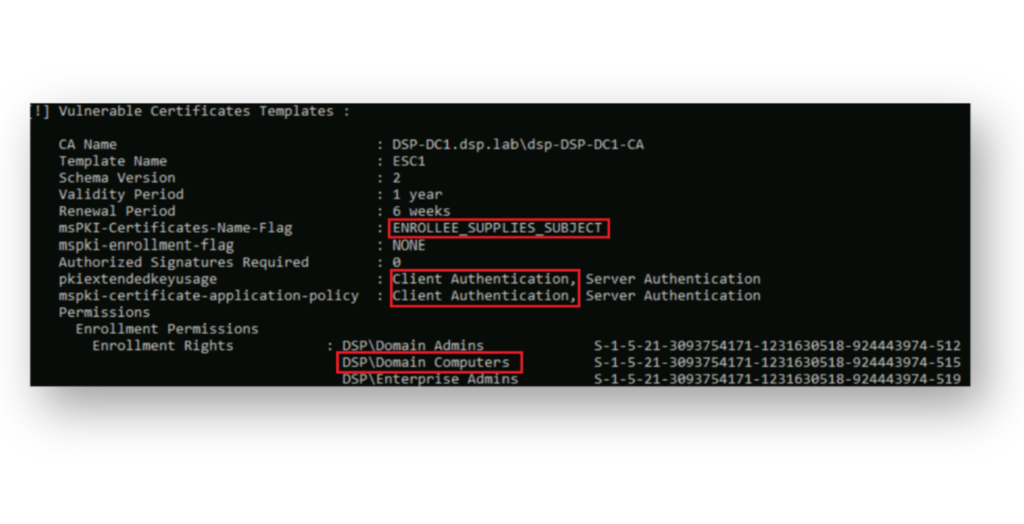
ENROLLEE_SUPPLIES_SUBJECT flag and Client Authentication EKU, creating a path for privilege escalation via ESC1.In our example, where Domain Computers are allowed to enroll in a vulnerable certificate template, an attacker can use Cable to create a new computer object (Figure 7) to take advantage of the default ms-DS-MachineAccountQuota setting and then request a certificate using that template.
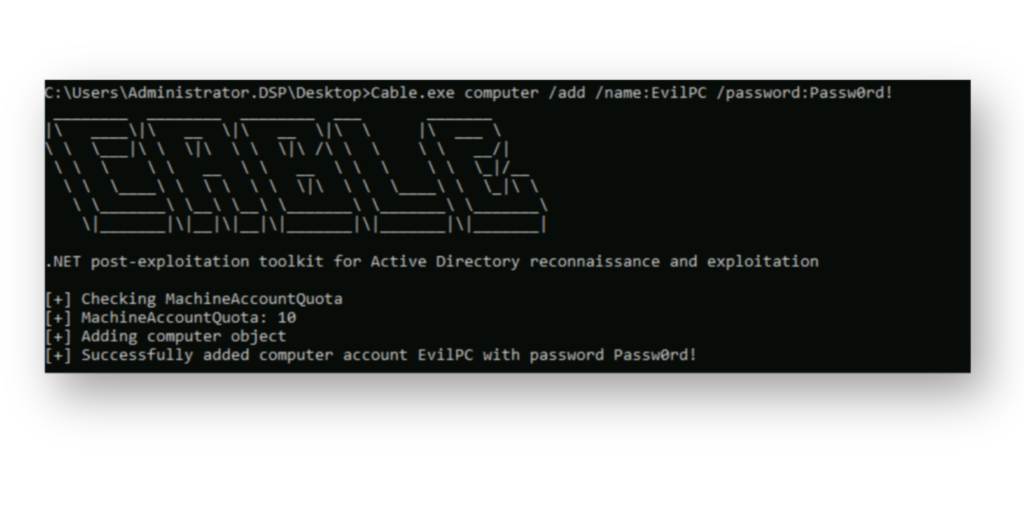
MachineAccountQuota setting.Furthermore, the attacker can now use runas.exe to authenticate as the newly created computer account and request a certificate from the vulnerable ESC1 template (Figure 8). This enables them to impersonate any user in the environment, including a Domain Admin.
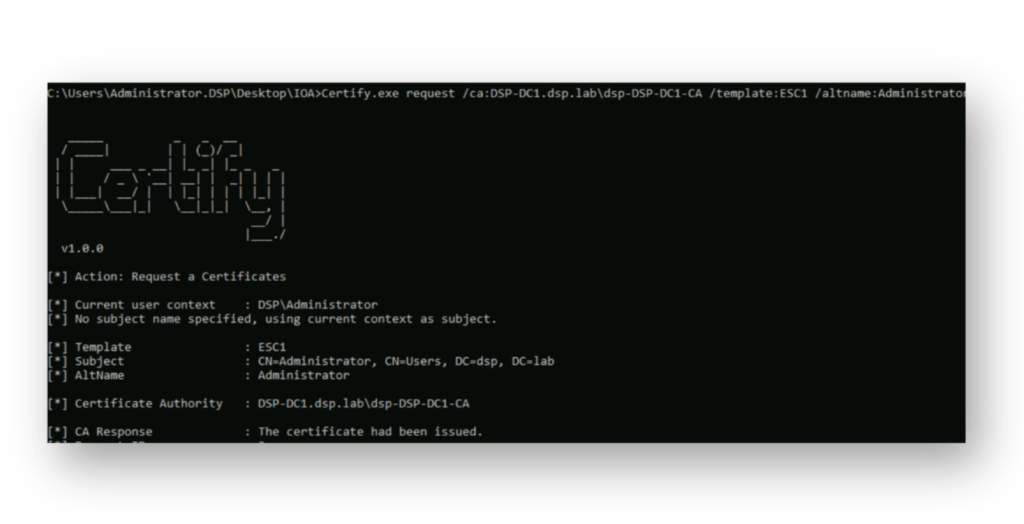
Within DSP, the recent change to Active Directory creating a malicious computer object has been successfully detected and logged (Figure 9).
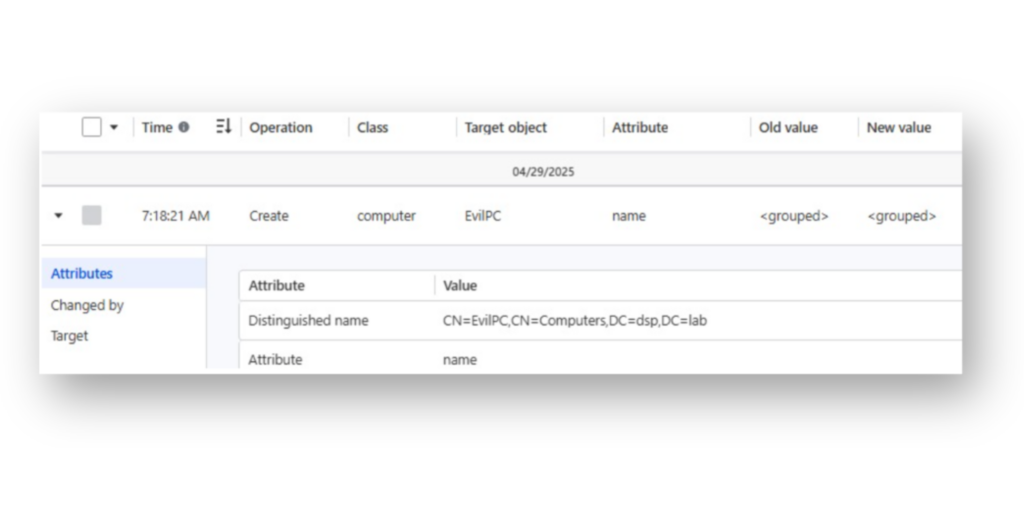
Now that Domain Admin privileges have been obtained, an attacker can use Cable to create an RBCD backdoor by modifying the target Domain Controller’s computer account. By adding their controlled computer object to the msDS-AllowedToActOnBehalfOfOtherIdentity attribute (Figure 10), they effectively grant themselves the ability to impersonate any user, including high-value targets to that system, at any time.
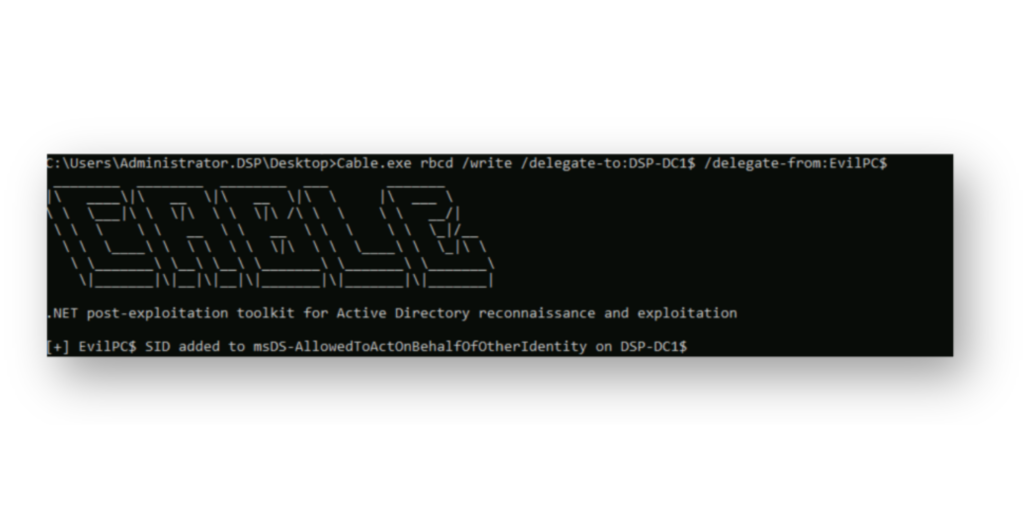
msDS-AllowedToActOnBehalfOfOtherIdentity attribute of the Domain Controller DSP-DC1$, effectively establishing an RBCD backdoor.Cable supports executing LDAP queries, which can be used to verify whether any accounts have a value set for the msDS-AllowedToActOnBehalfOfOtherIdentity attribute. As Figure 11 shows, the targeted Domain Controller reflects the configured delegation.
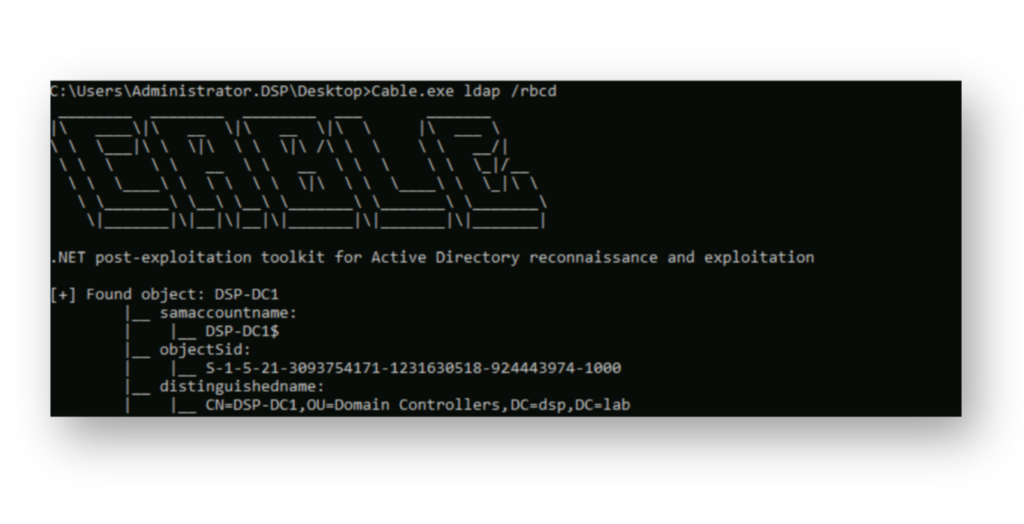
msDS-AllowedToActOnBehalfOfOtherIdentity attribute is set on the target Domain Controller DSP-DC1$, verifying that the RBCD configuration is in place.DSP has also successfully detected and logged the modification of the msDS-AllowedToActOnBehalfOfOtherIdentity attribute on the targeted Domain Controller’s computer account (Figure 12).
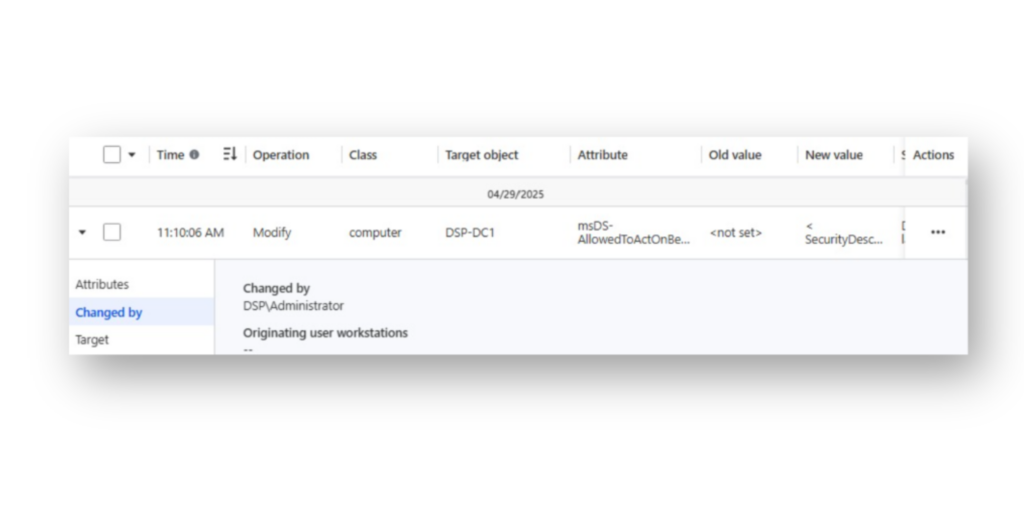
msDS-AllowedToActOnBehalfOfOtherIdentity attribute on the DSP-DC1 computer account, showing the exact change and the user responsible.Within DSP, the security descriptor set on this attribute is also parsed, allowing you to see exactly which computer account was added to msDS-AllowedToActOnBehalfOfOtherIdentity (Figure 13).
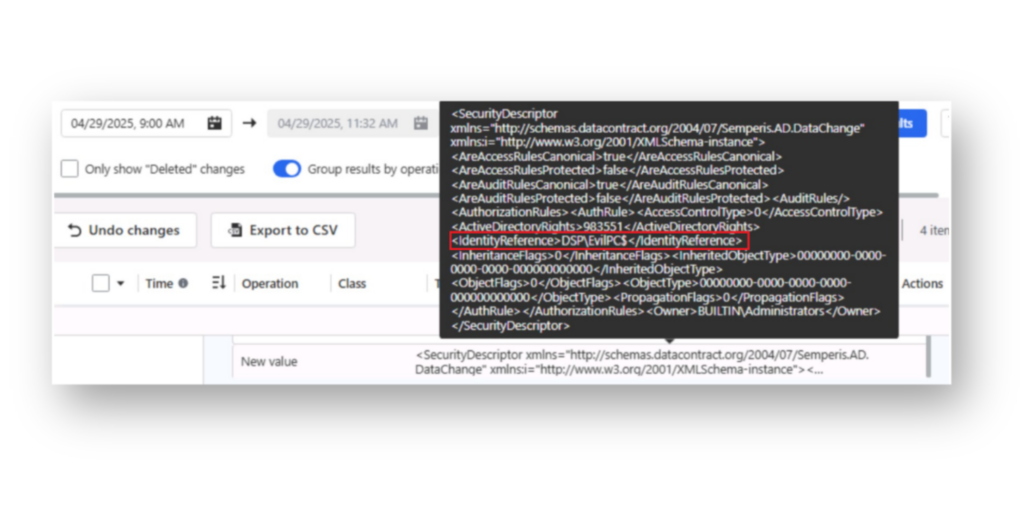
msDS-AllowedToActOnBehalfOfOtherIdentity attribute, clearly showing that the EvilPC$ computer account was added and confirming the presence of an RBCD backdoor.RBCD use case: Auto Undo Cable changes
DSP allows you to create alert and response rules, and since the msDS-AllowedToActOnBehalfOfOtherIdentity attribute should never be modified on a Domain Controller’s computer account, you can configure DSP to automatically detect this change and trigger an auto-undo action (Figure 14).
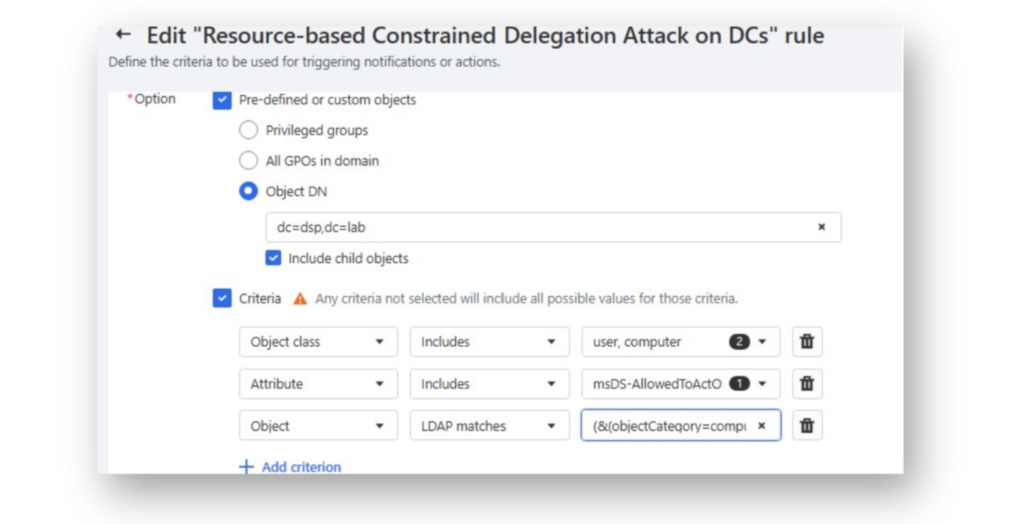
(&(objectCategory=computer)(userAccountControl:1.2.840.113556.1.4.803:=8192))Figure 15 shows an example of DSP performing an auto-undo action, automatically reverting the change back to its previous state.
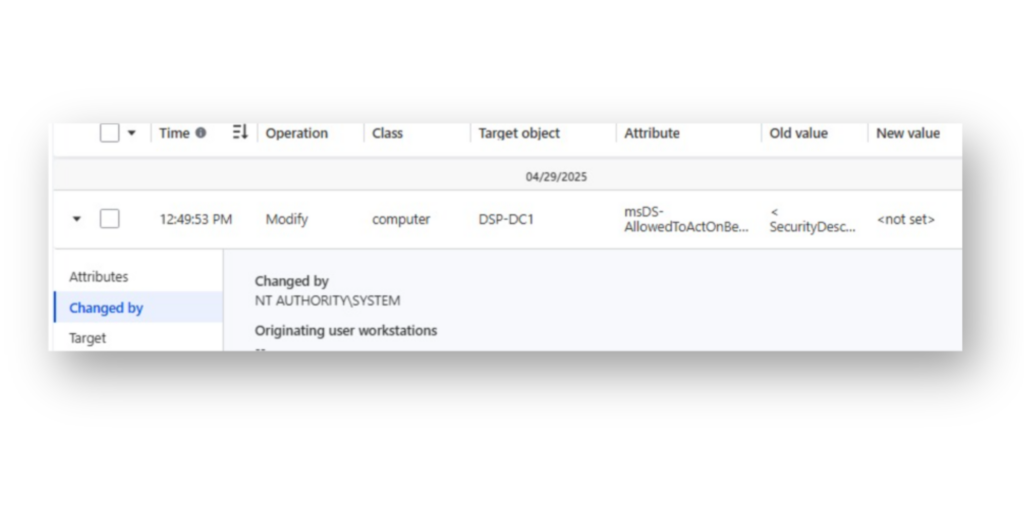
msDS-AllowedToActOnBehalfOfOtherIdentity attribute on the Domain Controller DSP-DC1.Semperis snapshot
Directory Services Protector provides organizations with visibility across the changes within their Active Directory environment. As we’ve demonstrated, DSP not only detects high-risk changes like the manipulation of sensitive attributes such as msDS-AllowedToActOnBehalfOfOtherIdentity but also responds to those changes automatically, reverting the unwanted changes back to the previous state.
