Windows Server 2025 introduces a new type of service account called delegated Managed Service Accounts (dMSAs). These accounts are designed to streamline service account management by giving administrators a secure and managed identity they can use to replace legacy unmanaged service accounts.
However, researchers at Akamai1 discovered that attackers can easily create and configure a dMSA, then abuse it to impersonate any user in Active Directory—including Domain Admins. The researchers named this technique BadSuccessor.
Because no patch exists yet for this vulnerability, Semperis has enhanced Directory Service Protector (DSP) with an indicator of exposure (IOE) and three indicators of compromise (IOCs) focused on enabling you to detect and mitigate malicious activity involving dMSAs.
What is BadSuccessor?
BadSuccessor is a privilege escalation technique that exploits dMSAs by granting high-privilege permissions to any user who creates a dMSA object.
Creating a dMSA is relatively simple.2 And as the Akamai team demonstrated, once the object is created, an attacker can run a simulated migration, linking the dMSA to any high-privilege account.
Setting specific attributes during account creation causes the domain controller (DC) to treat the dMSA as if it’s continuing the identity of a privileged user, leading to Privilege Attribute Certificate (PAC) exploitation.
The dMSA feature is present by default in any Windows Server 2025 DC and carries significant risk.3
- With minimal permissions, attackers can create a dMSA and link it to a privileged account.
- Gaining instant access, attackers can quickly compromise the entire domain.
- Because legacy delegation rights are typically complex and layered, exploitation of the vulnerability is hard to detect.
Clearly, proactive mitigation is essential.
Defend against BadSuccessor: New DSP indicator of exposure
All DSP-I customers will get an updated IOE list, which now includes a new check that looks for Active Directory (AD) accounts with excessive permissions (Figure 1).
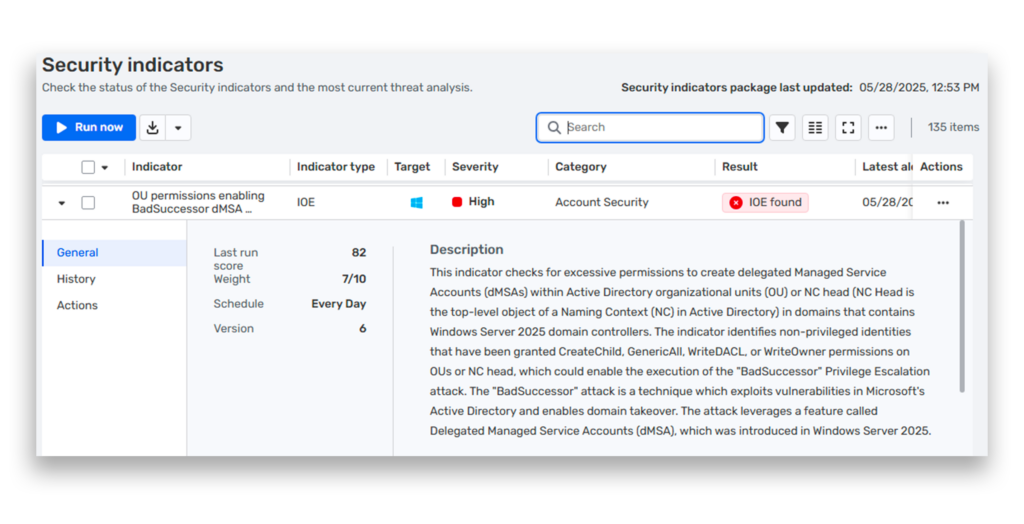
This isn’t just about BadSuccessor. Broad permissions can lead to all kinds of unintended escalation paths. In many environments, delegation is used with convenience or operational pressure in mind. Over time, the practice results in accounts with far more access than they should have—and easy opportunities for attackers.
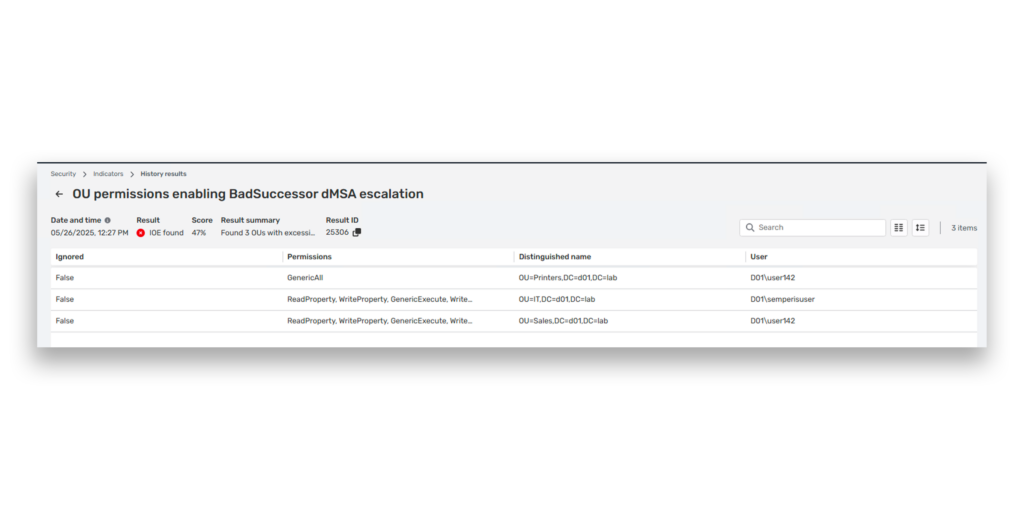
The screenshot in Figure 2 shows sample results from the DSP IOE detecting excessive organizational unit (OU) permissions related to the BadSuccessor dMSA vulnerability. The list shows OUs in which users have been granted overly broad permissions, such as GenericAll or multiple write rights that could allow them to create or manipulate dMSAs.
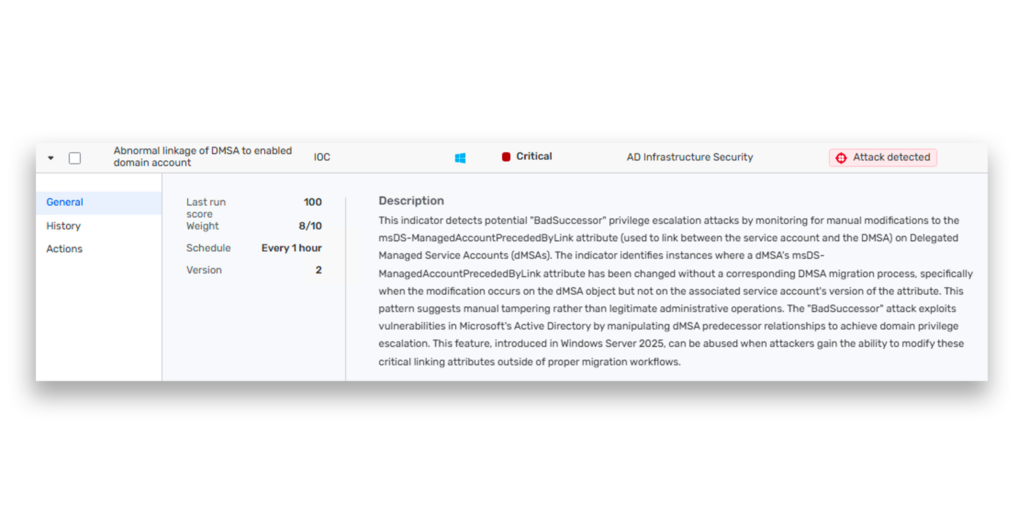
Detecting BadSuccessor activity: New indicators of compromise
In collaboration with Akamai, we’ve added three new IOCs in DSP. The first indicator flags cases where the msDS-ManagedAccountPrecededByLink attribute on a dMSA is modified outside of a proper migration (Figure 3).
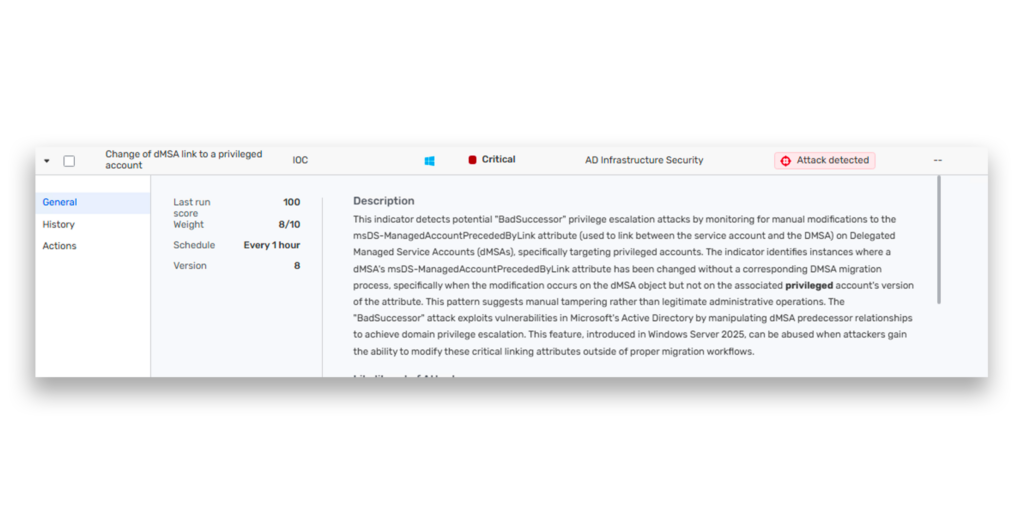
The second IOC detects when a dMSA is manually linked to a privileged account outside of a proper migration, a sign of potential BadSuccessor abuse to escalate domain privileges (Figure 4).
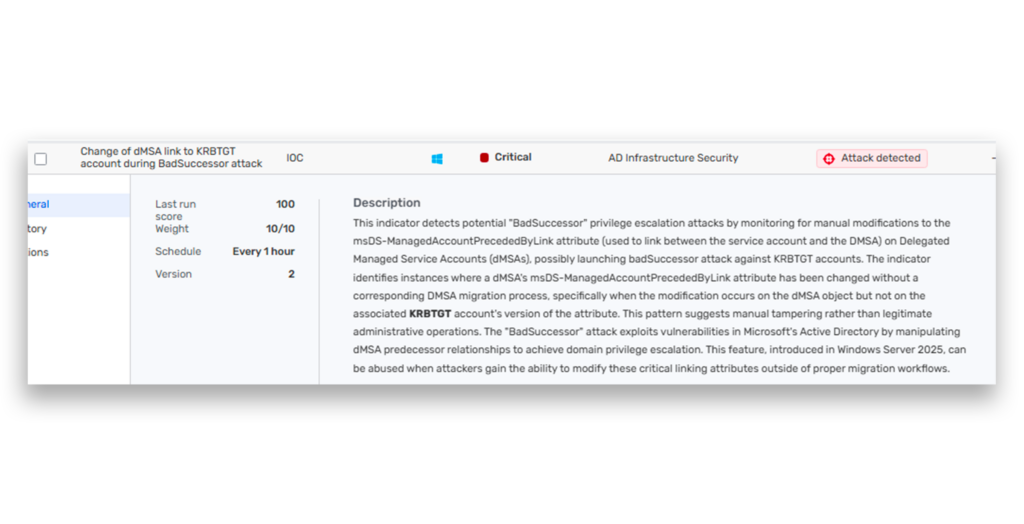
The third IOC detects attempts to link a dMSA to the KRBTGT account (Figure 5).
Semperis snapshot
BadSuccessor specifically affects organizations that have at least one DC running Windows Server 2025.
Even if the rest of the domain is running older versions, a single 2025 DC is enough to make the attack path viable.
Until Microsoft releases a patch, the most effective mitigation is reviewing and tightening permissions in AD, particularly those that allow users to create or modify dMSAs.
Focus on rights granted to OUs and the Domain Root object, which are often excessive due to overly broad delegation practices.
DSP’s IOEs and IOCs help enable close monitoring of dMSA creation and authentication events as well as attribute modifications.
Learn more about the dangers of excessive privileges in AD
- Why You Should Pay Attention to Excessive Privilege in Active Directory – Semperis
- What is Unconstrained Delegation? | Semperis Identity Attack Catalog
- What Is Active Directory Security? | Semperis AD Guides
- Tiered Delegation and ACL Management | Semperis Guides
