The intruder’s dilemma is the flip side of the defender’s dilemma, which explains the challenges of cybersecurity defense. While Active Directory (AD) defense against every possible attack technique is the challenge for defenders, attackers have a different problem: once they break in, they have to avoid getting caught.
Attackers may need to find only one weakness to gain access, but staying undetected is much harder. They need to maintain access, move laterally, escalate privileges, and execute their objectives without triggering alarms or getting locked out.
What if we could turn that intruder’s dilemma to our advantage?
How to turn an attack into a practical AD defense
Understanding the ways bad actors look for and use vulnerabilities is critical for AD defense. To illustrate the value of this knowledge, let’s single out a common identity attack method that leverages certificate misconfigurations.
Attacks against Active Directory Certificate Services (AD CS) have gained significant attention after SpecterOps published research on how misconfigurations in AD CS can be exploited for privilege escalation and persistence. Their Certified Pre-Owned report1 outlined multiple techniques, including ESC1, ESC4, and Golden Certificates, which allow attackers to abuse certificate-based authentication to compromise privileged accounts. Since this research was released, threat actors and red teams have increasingly weaponized these techniques,2 making AD CS a high-value target.
This is where defenders can turn the tables. When you set up a honeypot—like a decoy certificate template that appears vulnerable—attackers are forced to make a choice. They can either attempt to exploit what looks like a misconfiguration, risking exposure in the process, or ignore it and look for another way to escalate privileges.
Imagine an attacker scanning for misconfigured certificate templates finds one where they have modification rights. They can attempt to enable the Supply in Request option, which would allow them to specify a privileged identity in a certificate request.
The trap is set.
DISCLAIMER: Deploying a decoy CA template and intentionally making it vulnerable to attacks like ESC1 and ESC4 does expand the attack surface. However, with the right security mechanisms in place to detect and remediate these threats, it can be an effective approach.
Creating a honeypot trap with a decoy certificate template: Example 1
Figure 1 shows what an attacker finds when using a tool like Certify3 to scan for exploitable certificate templates.
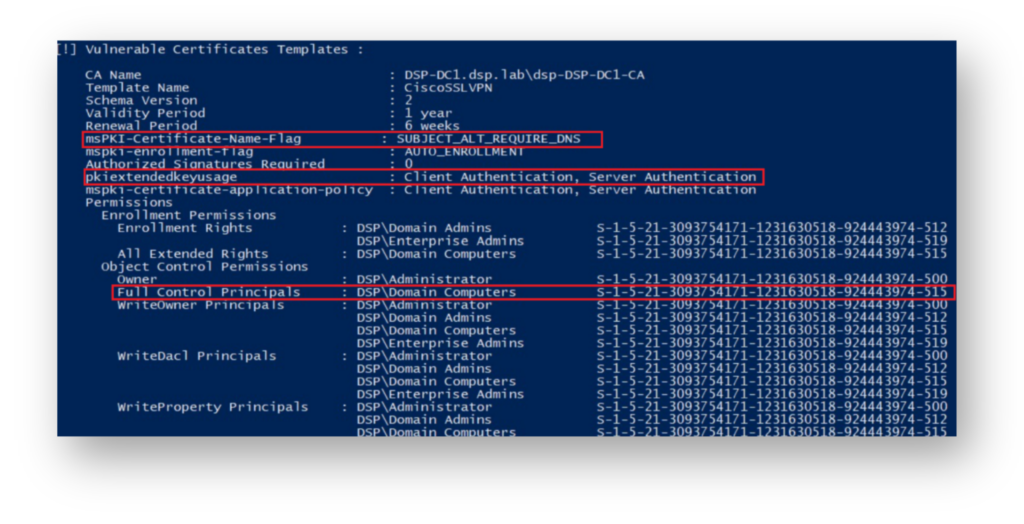
This certificate, CiscoSSLVPN, supports Client Authentication and allows Domain Computers to enroll. But since msPKI-Certificate-Name-Flag isn’t set to ENROLLEE_SUPPLIES_OBJECT, the ESC1 attack won’t work.
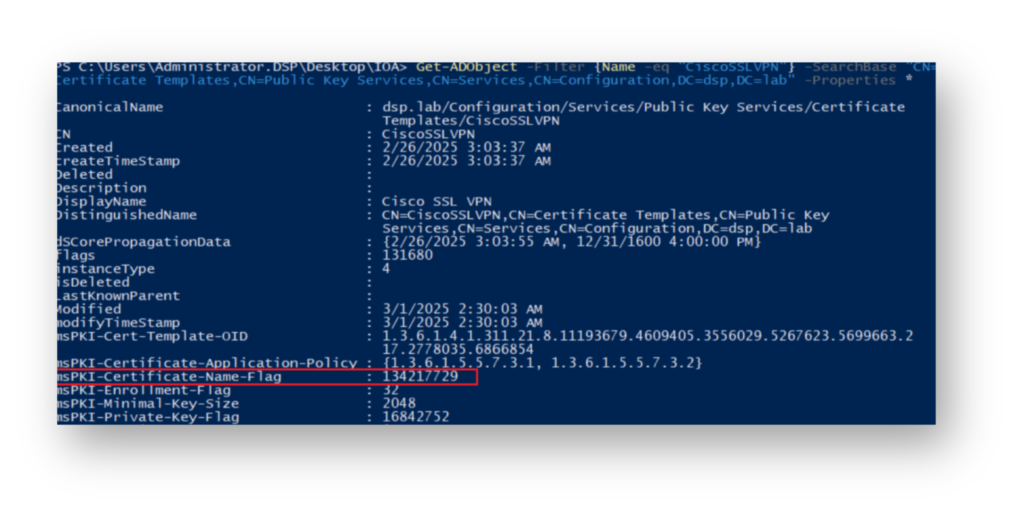
When the attacker looks at the AD attributes of the CiscoSSLVPN certificate (Figure 2), they see that the msPKI-Certificate-Name-Flag value is set to 134217728, which corresponds to SUBJECT_ALT_REQUIRE_DNS. This means that the Supply in Request option is not enabled.
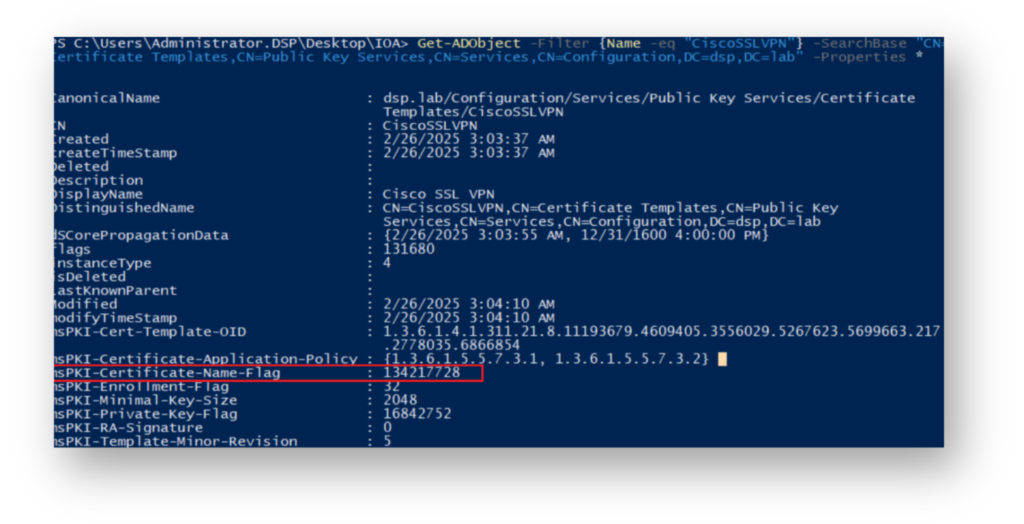
CiscoSSLVPN certificate template attributes, with msPKI-Certificate-Name-Flag set to 134217728, indicating SUBJECT_ALT_REQUIRE_DNS.Since in this example, we granted Domain Computers Full Control over this CA template, our attacker could take advantage of msDs-MachineAccountQuota (Figure 3), which is set to 10 by default, to create a new computer object, authenticate as the computer account, and then modify the CA Template.
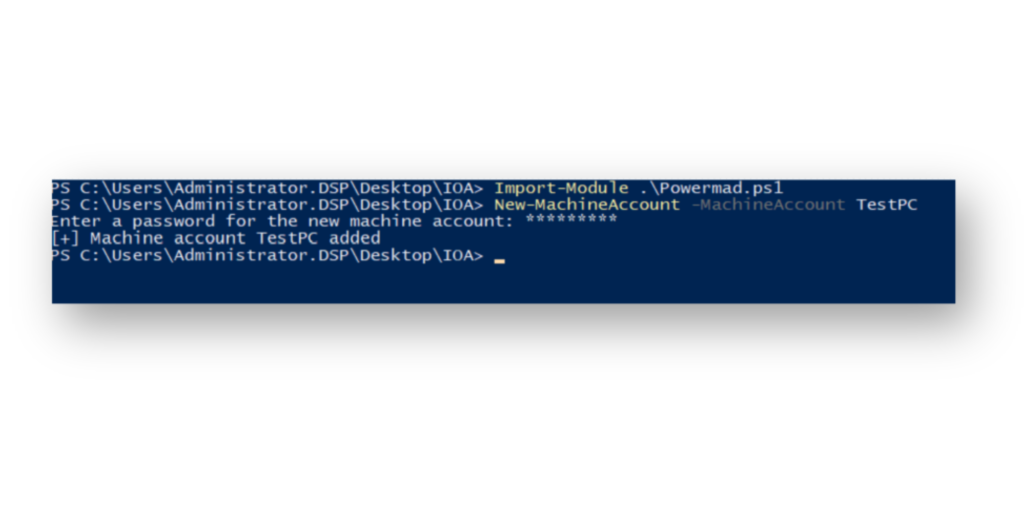
TestPC) by leveraging msDs-MachineAccountQuota, which is set to 10 by default in AD.Next, the attacker authenticates as the computer account and modifies the CA template to make it vulnerable to ESC1 (Figure 4).
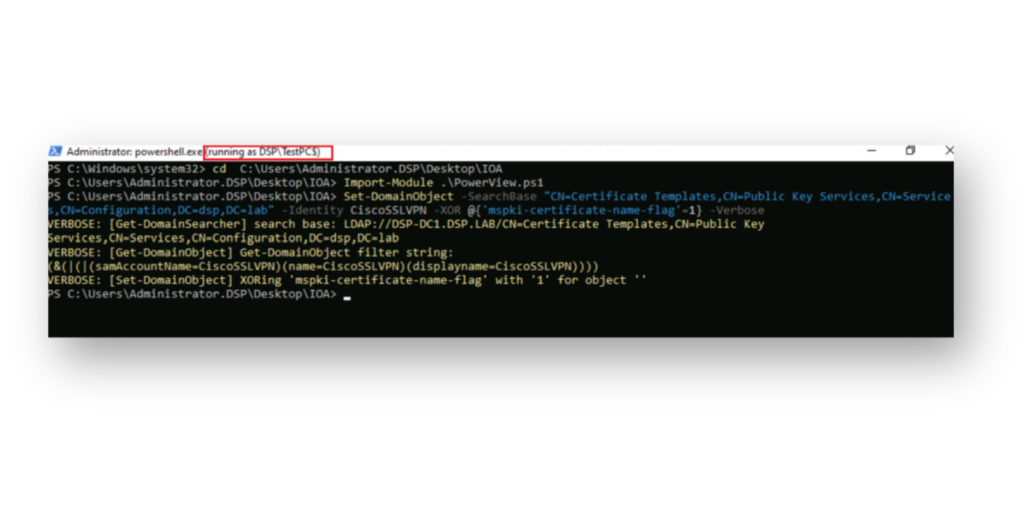
TestPC$ machine account, modifying the msPKI-Certificate-Name-Flag on the CiscoSSLVPN certificate template to make it vulnerable to ESC1.Now, our attacker checks the AD attributes of the modified CA template. They see that the msPKI-Certificate-Name-Flag value has changed (Figure 5), which reflects the modification that makes it exploitable.
CiscoSSLVPN certificate template, where the msPKI-Certificate-Name-Flag value has changed, making it vulnerable to ESC1.On the AD defense side: In Directory Services Protector (DSP), you can now see an entry logging the AD change on the decoy CA template (Figure 6), highlighting the specific attribute that was modified.
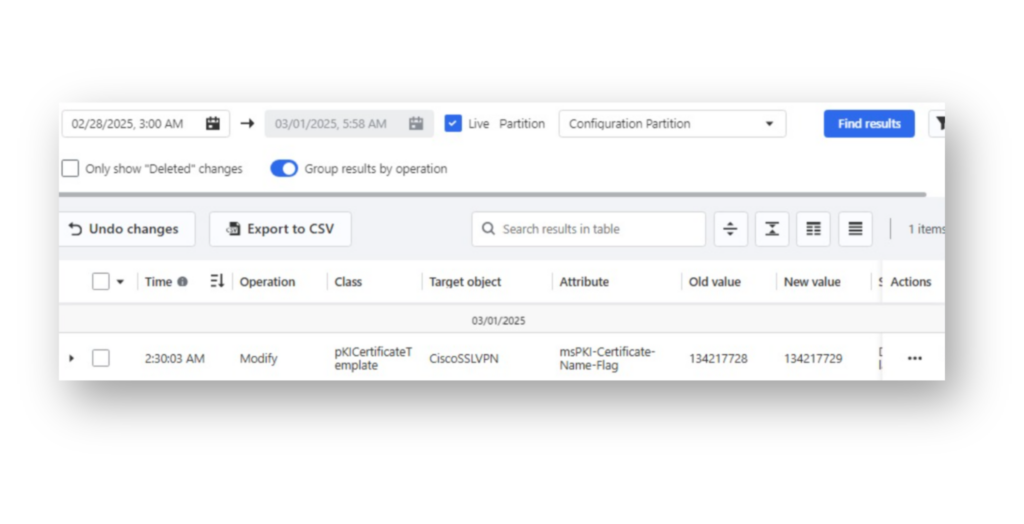
CiscoSSLVPN certificate template, where the msPKI-Certificate-Name-Flag value was changed, allowing further investigation into the account responsible for the action.DSP also shows who modified the CA template (Figure 7), allowing you to investigate the account responsible for the change and detect any further suspicious activity.
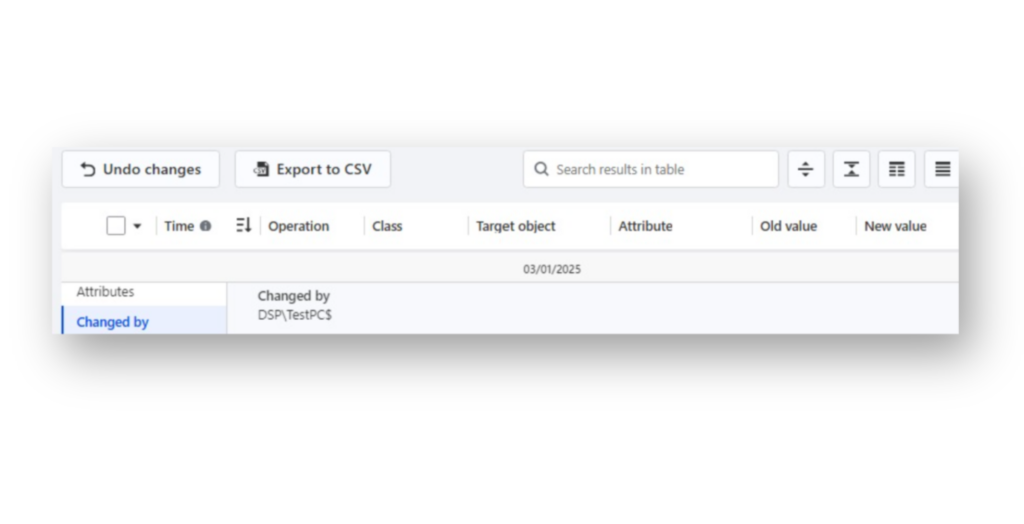
CiscoSSLVPN certificate template was modified by the TestPC$ computer account.Creating a honeypot trap with a decoy certificate template: Example 2
The WebServer certificate template is commonly used to issue SSL/TLS certificates for Windows Server Update Services (WSUS), Active Directory Federation Services (ADFS), Internet Information Services (IIS) web servers, and load balancers. It ensures encrypted communication over HTTP. By default, it is configured with Supply in Request, but since the Extended Key Usage (EKU) is set to Server Authentication, ESC1 can’t be exploited (Figure 8).
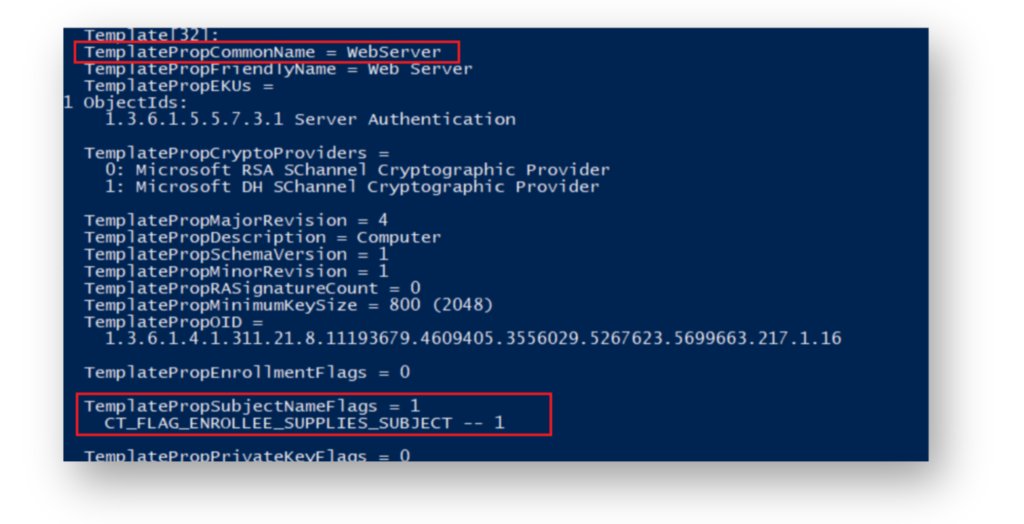
WebServer certificate template, showing that Supply in Request (CT_FLAG_ENROLLEE_SUPPLIES_SUBJECT) is enabled, but the EKU is set to Server Authentication.To set our trap, you can begin by duplicating the WebServer template and giving it a realistic name to make it appear legitimate. Then, modify the DACL to make it look like a legitimate configuration by allowing a fake computer account, such as WSUS-2016, to enroll.
At the same time, intentionally misconfigure the template by granting Write permissions to Authenticated Users (Figure 9), which creates an opportunity for exploitation.
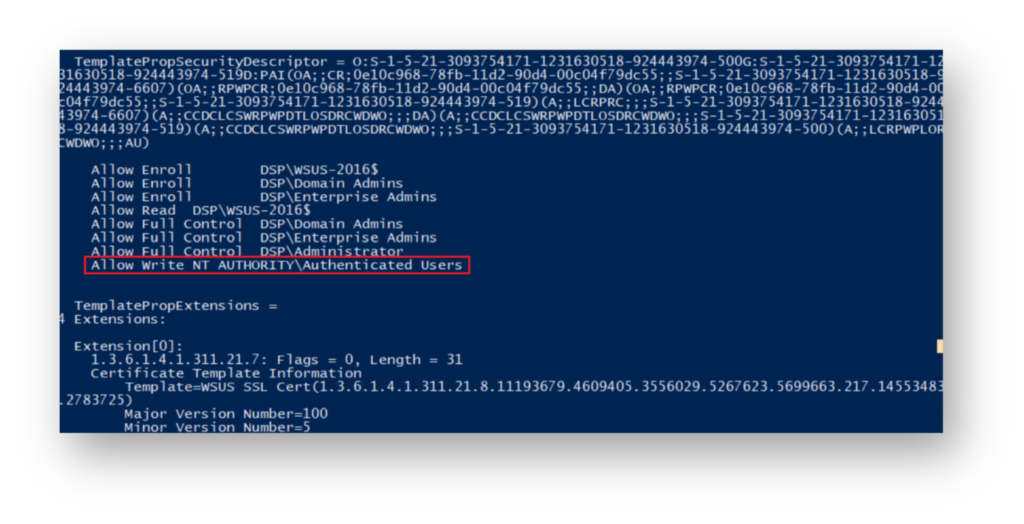
WSUS-2016$) has Enroll permissions, and Authenticated Users have been misconfigured with Write permissions, making the template vulnerable to exploitation.Figure 10 shows what reconnaissance looks like to an attacker identifying exploitable CA templates, where Authenticated Users have Write permissions on the decoy WSUSSSLCert template.
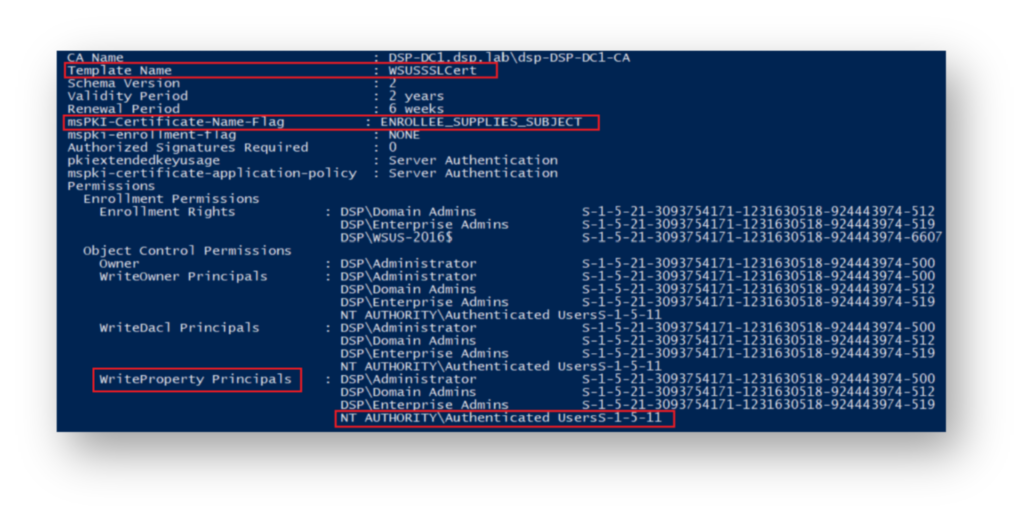
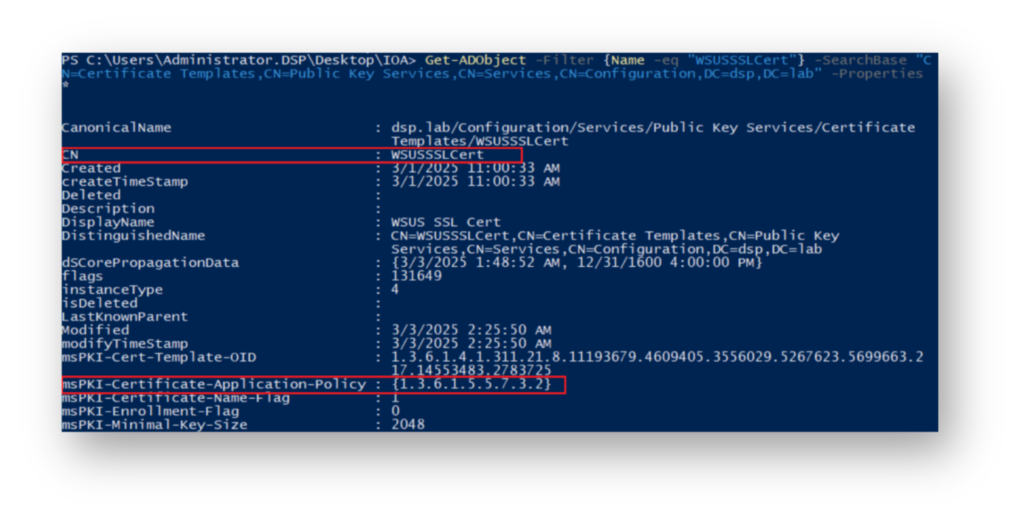
WSUSSSLCert certificate template, where Authenticated Users have WriteProperty permissions, allowing them to modify attributes such as EKU.Now, our attacker examines the current AD attribute values of this CA template, focusing specifically on the msPKI-Certificate-Application-Policy value, which defines the allowed certificate usage (Figure 11).
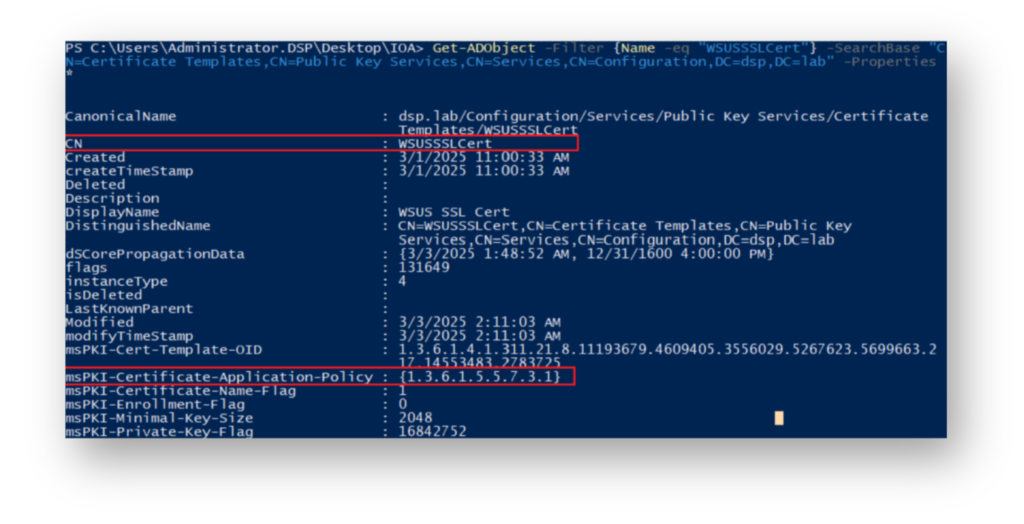
WSUSSSLCert certificate template, highlighting the msPKI-Certificate-Application-Policy value. The Object Identifier 1.3.6.1.5.5.7.3.1 corresponds to Server Authentication.Now, they modify this CA template to make it ESC1 exploitable, then check how the msPKI-Certificate-Application-Policy value changes (Figure 12).
WSUSSSLCert certificate template, where the msPKI-Certificate-Application-Policy was changed to 1.3.6.1.5.5.7.3.2, enabling Client Authentication. This change makes the template vulnerable to ESC1.As Figure 13 shows, the msPKI-Certificate-Application-Policy attribute has been updated to a different Object Identifier, now corresponding to Client Authentication.
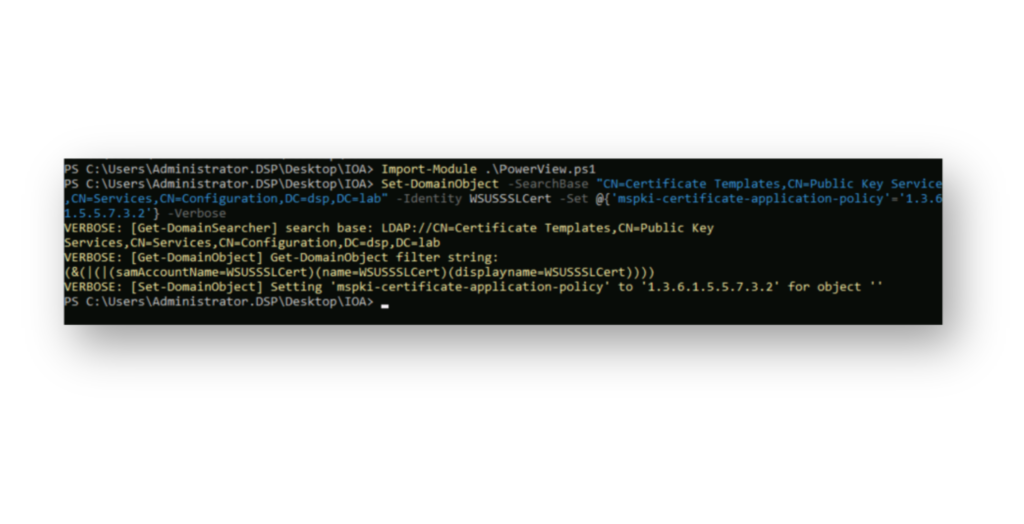
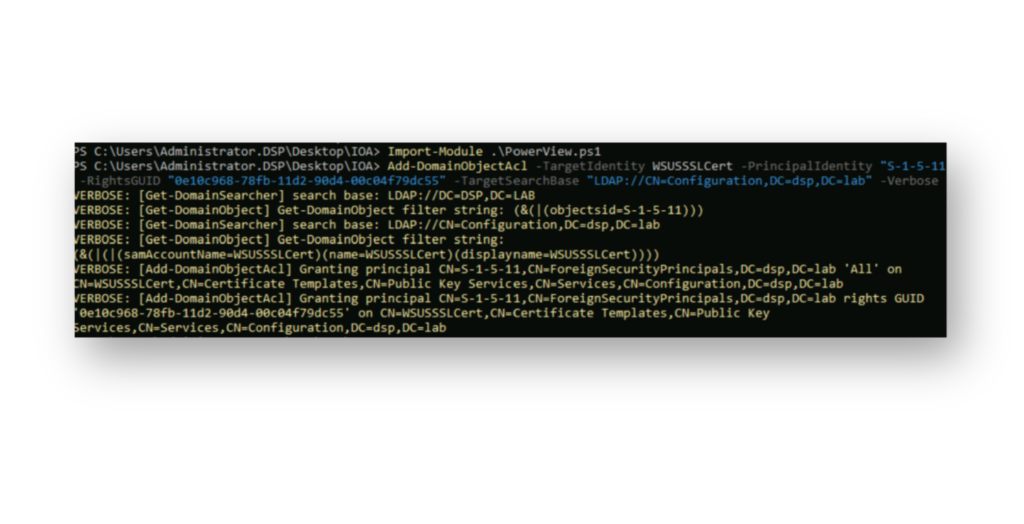
WSUSSSLCert certificate template, where the msPKI-Certificate-Application-Policy has been changed to 1.3.6.1.5.5.7.3.2, enabling Client Authentication. Now, the template is not just vulnerable but is also exploitable for ESC1.The final step our attacker takes is to grant enrollment permissions on the CA template, enabling them to exploit it (Figure 14).
WSUSSSLCert template using PowerView.On the AD defense side: In DSP, there is now an entry in the AD changes log indicating that someone has modified this specific AD attribute on the CA template (Figure 15).
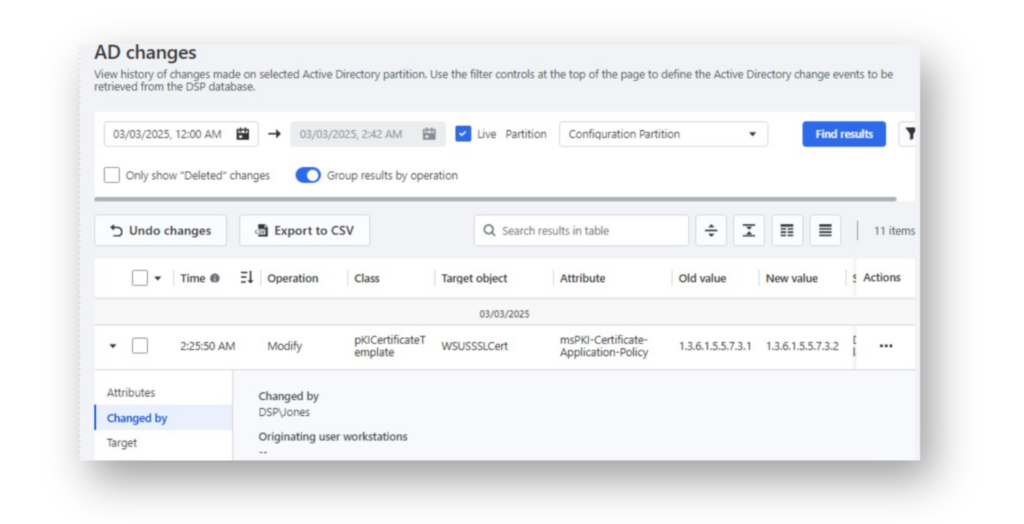
WSUSSSLCert certificate template, where the msPKI-Certificate-Application-Policy value was changed from Server Authentication to Client Authentication.Another entry will be logged in DSP indicating that the Security Descriptor attribute was modified on the decoy CA template (Figure 16).
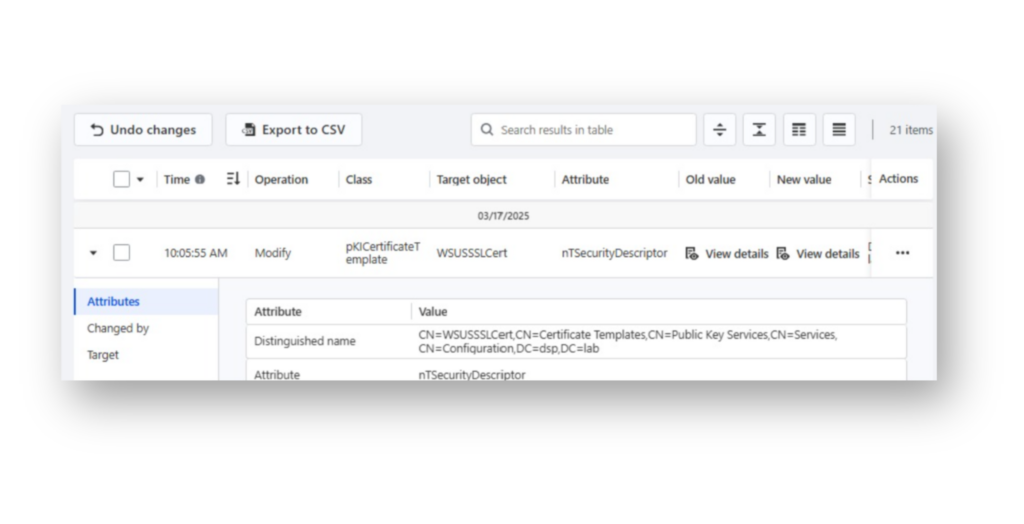
WSUSSSLCert CA template.The key to decoys in AD defense: Create a notification rule in DSP
In DSP, you can create a notification rule for decoy certificate templates (Figure 17) so that any changes made to them will trigger an alert.
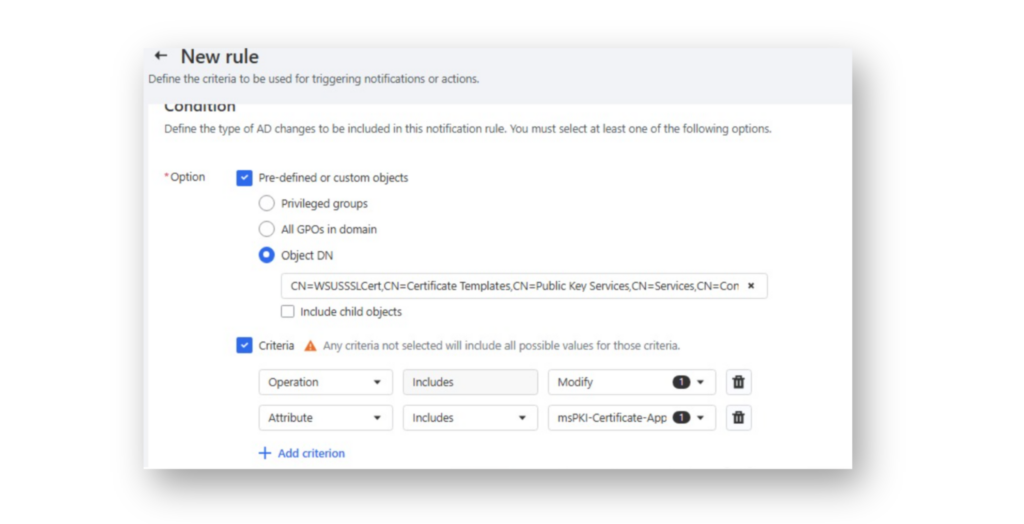
WSUSSSLCert certificate template, is configured to trigger an alert whenever a modification is made to the msPKI-Certificate-Application-Policy attribute.Once someone modifies this AD attribute on the decoy CA template, DSP will send an email notification including details about who made the change, which Domain Controller it occurred on, and other relevant information (Figure 18).
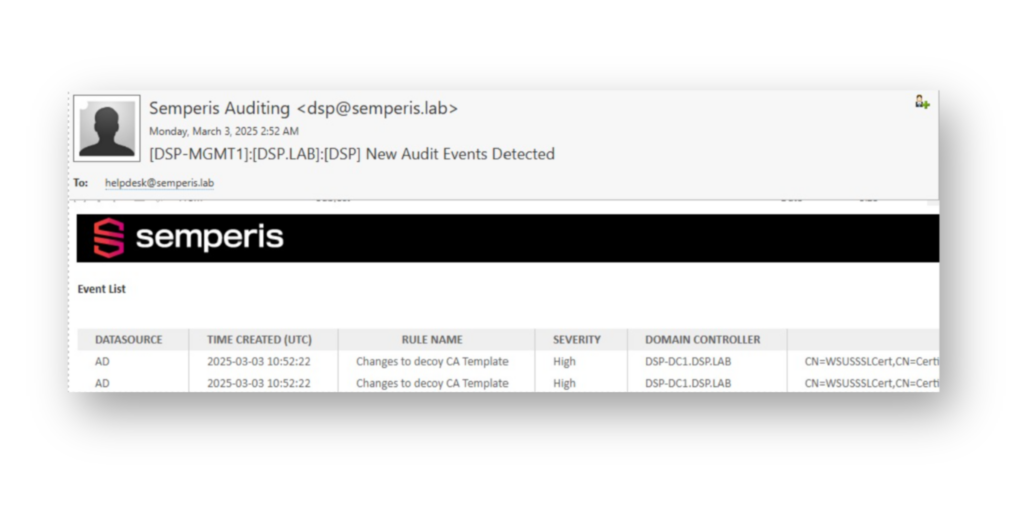
Semperis snapshot
For organizations running ADCS, setting up honeypot traps can be a valuable way to detect attackers before they can escalate privileges. ADCS misconfigurations are increasingly exploited in real-world attacks, as highlighted by Mandiant’s report4 on Ivanti post-exploitation tactics. By deploying decoy certificate templates that appear vulnerable but are closely monitored, AD defenders can lure attackers into revealing themselves the moment they attempt exploitation.
Learn more about proactive Active Directory defense
- NSA Top Ten Cybersecurity Misconfigurations: An Active Directory Perspective
- Cyber Resilience 101: Top Tips for AD Defense
- What Is Active Directory Security?
- Active Directory Hardening Best Practices
