Because Active Directory offers both broad and deep control across your Windows ecosystems, cyber attackers are constantly seeking AD entry points. One of the easiest ways for cyber attackers to gain access to your identity system is through guessing an account password or obtaining one through phishing, social engineering, or password spraying. Next best? An encrypted password that’s easy to decode.
For this reason, any credential feature that provides an easy pathway to learning a password is not recommended. That’s the case with Group Policy Preferences (GPP).
What is the Group Policy Preferences feature?
Group Policy Preferences is a Windows feature that lets administrators manage settings for multiple machines across an Active Directory (AD) domain. With GPP, admins can control things like mapped drives, scheduled tasks, and registry settings.
At one point, GPP also allowed passwords to be set for local accounts (Figure 1), but this practice was insecure as it allowed storing of passwords in an easily reversible format. Microsoft eventually removed that capability.
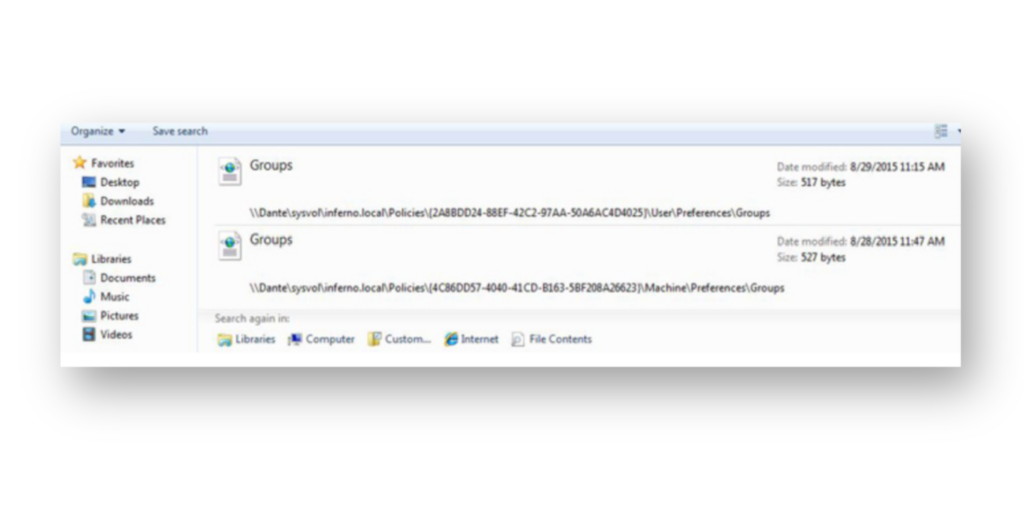
How are Group Policy Preferences abused?
Figure 2 shows an example of a GPP XML file that stored the password for the local Administrator account. The password, shown as cpassword, is encrypted but was easily decoded because the encryption key is publicly disclosed and well known—which led to major security risks. In addition, passwords set in GPP could be applied across multiple workstations and member servers. That meant the local Administrator account on each of those systems would have the same password set by the cpassword value in the XML file.
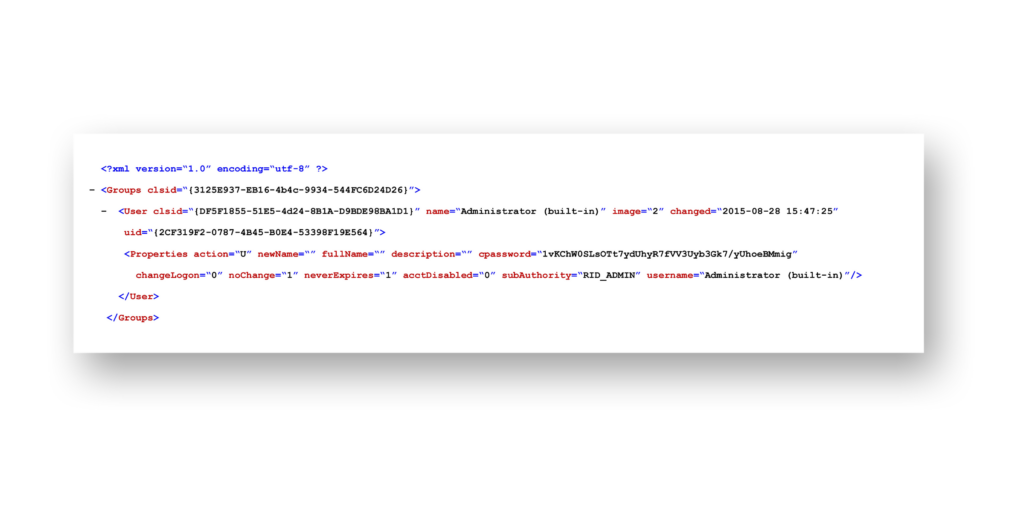
cpassword), which could be easily decrypted.How can you detect and defend against GPP abuse?
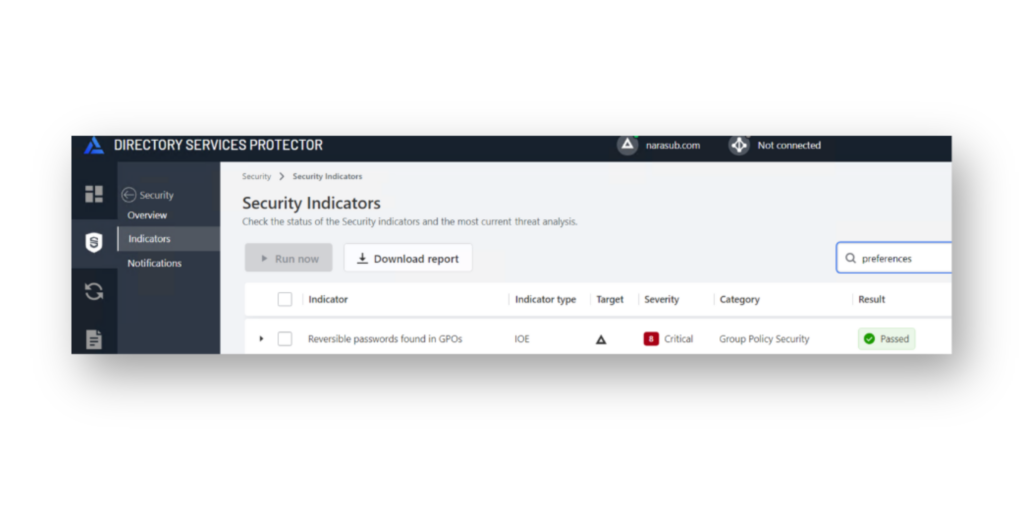
Semperis Directory Services Protector (DSP) includes an indicator of exposure that continuously monitors and detects any potential password files in Group Policy Preferences (Figure 3).
Threat actor profiles
The following threat actors have been searching for passwords in Group Policy Preferences:
- Wizard Spider (MITRE Group G0102)1
- APT33 (MITRE Group G0064)2
- BlackCat3
GPP abuse tools
The following tools can be utilized to search for passwords in Group Policy Preferences:
- PowerSploit
- Net-GPPPassword Get-GPPPassword
Threat overview
ATT&CK Tactic: Credential Access
On October 18, 2023, Palo Alto Networks Unit 42 reported that BlackCat, a ransomware gang, introduced a new tool called Munchkin. This tool was delivered through a customized Alpine virtual machine and contains various Python scripts, including Get-GPPPassword.py. Attackers used this tool to find and exploit stored passwords in Group Policy Preferences.4
On March 27, 2019, Symantec reported that APT33 (Elfin) attempted to use the Gpppassword tool to find and decrypt passwords stored in Group Policy Preferences. While it’s not clear if these attempts were successful, the group aimed to exploit misconfigured GPP settings to extract plaintext passwords and move laterally through targeted networks.5
Semperis snapshot
In 2014, Microsoft released security bulletin MS14-025 providing security updates to fix the security risks with GPP. However, applying MS14-025 updates merely prevents new password-setting policies; it doesn’t remove old policies still storing passwords in SYSVOL. You can clean up those existing policies by using Microsoft’s Get-SettingsWithCPassword.ps1 script, which finds and deletes any exposed passwords.
Switching to Windows Local Administrator Password Solution (Windows LAPS) or any other privileged access management solution is a better way to manage local Administrator passwords, ensuring each machine has a unique password and preventing attackers from moving laterally.
Learn more about credential compromise risks
- Password Spraying Explained
- Group Policy Abuse Explained
- Active Directory Attacks | 5 Common AD Attack Methods
- NSA Top Ten Cybersecurity Misconfigurations and Active Directory
